Cybersecurity

Feature "DDoS"
IoT – Pioneering in a Weird Diversified Landscape
The Mirai botnet, making IoT secure, and risks & benefits of e-health: Interview with Peter Meyer, Head of Cyber Security Services at the eco Association

Feature "Quantum Computing"
Quantum Computing and the Future of Encryption
Quantum computing may still be some years from its breakthrough, but we should be preparing now for security in the post-quantum era

Feature "Cybersecurity"
Fight Against Spam and Cyber Attacks: How Brands Can Authenticate Their Emails Using DNS Records
Thomas Küchenthal, CTO of LEMARIT, explains the risks brand owners run with missing DNS records and why they are so important for preventing spam, spoofing, and other security risks.

Feature "Cybersecurity"
A Day in the Life of a Cyber Policeman
What gives cyber policemen sleepless nights? Dirk Kunze talks about serious cyber crime and seriously terrifying cyber crime
Industry Insights "Cybersecurity"
Cyber Security in the EU

Feature "DNS"
Navigating the Digital Landscape: DNS Security in the Modern Age of Cyber Threats
Nameshield’s CPO Christophe Gérard emphasizes the crucial role of DNS in Internet security and explores emerging trends to protect your online presence.

Feature "E-Health"
Hospitals in the Focus of Cyber Criminals
Personal health information (PHI) is increasingly a target for cyber criminals - Hans-Peter Bauer from Intel Security explains why

Feature "Company Security"
Building IT Defenses – Keeping the Wolves from the Company Gate
What’s your bottom line? Cyber attacks against companies range from the sophisticated to the ingeniously simple – and it could be your competitive advantage on the line.
Industry Insights "Company Security"
Cyber Crime Against Companies – There’s Money to be Made
Proactive Hunting for Hidden Threats using Metadata

Feature "Domains"
To block or takedown: How to treat malicious activity on the Internet?
Billions are lost annually to cybercrime. Malware, phishing, ransomware—threats loom large. Sven Krohlas, a Detection Engineer at Spamhaus Technology Ltd, delves into the critical need for companies to recognize the threats posed by malware and phishing attacks.
Feature "E-Health"
Alternative Authentication Approach to Medical Devices
Markus Hertlein, XignSys, and Matteo Cagnazzo, if(is), explore solutions for securing and ensuring only authorized access to private health data.

Feature "Cybersecurity"
Gender Cyber Gap: How Strong is the Glass Firewall for Female Hackers?
At eco’s Internet Security Days, Catrin Schröder-Jaross and Christiane Schmidt from adesso SE exposed the persistent gender bias in cybersecurity. Through personal stories and data, they highlighted the need for more inclusive and bias-free cybersecurity environments.

Feature "E-Health"
Reigning in Toddler Technology – Making E-health Safe
E-health is still in its infancy – how can we ensure that the benefits are not outweighed by the risks to life, limb and privacy?
Industry Insights "E-Health"
Securing Intelligent Healthcare
Who Wants to Get Hold of Your Health Data?
Open and Secure Communication Platforms for Cooperation and Innovation
Ambient Assisted Living in the Zelia Project: Lessons Learned
Alternative Authentication Approach to Medical Devices
Hospitals in the Focus of Cyber Criminals

Feature "Blockchain"
Security and Privacy in Blockchain Environments
Matteo Cagnazzo and Chris Wojzechowski, both researchers at the Institute for Internet Security, explore how security and privacy can be enhanced by blockchain technology.

Feature "Cybersecurity"
Fortifying Cyberspace: How Innovative Companies from Canada’s Ontario are Protecting Us Against Cyber Attacks
Kathrin Seitz, Ontario Trade and Investment Office, Munich & Philipp Kornitzky, Government of Ontario, on the Province’s robust cybersecurity sector.

Feature "Cybersecurity"
IT Security in SMEs – Closing the Gap
Jens Kroppmann, Head of the Security Operation Center within CONET, explains how an SOC can support SMEs in rapidly detecting and mitigating cyber attacks.

Feature "Cybersecurity"
Prospects for a Future in Digital Communication – What About Security?
Hannah Kreyenberg from Hornet Security on the importance of email security for the success of digitalization and the protection of company assets.

Feature "Brands"
Control Your Digital Brand: On the Interplay of Defensive Domain Registrations, Active Monitoring, and Brand Enforcement
Verena Kuthe from LEMARIT outlines the path to retain full control of digital brands through the best brand protection approach.

Feature "Cloud Computing"
Cyber Security from the Cloud – Offering SMBs Enterprise-Grade Security
The BSI’s yearly report on cyber security paints a bleak picture. But there is a ray of hope, reports Roger Scheer from Veronym.

Feature "Cybersecurity"
The Human Element of IT Security
Human behavior can undermine the development of an effective IT security culture in companies at home and abroad. In particular, cultural differences in the approach to IT security must be taken into account in order to mitigate possible risks.

Feature "Email Best Practices"
DMARC - Protecting Your Infrastructure and Users from Phishing Attacks
Technical measures have been standardized to make phishing attacks less successful, Sven Krohlas from BFK explains – they just need to be implemented.

Feature "Domains"
Your Digital Storefront: Protecting Your Domain Name and Choosing the Right Registrar
Join Joëlle Samaké and Arnaud Wittersheim from Nameshield as they look at the pivotal role of domain names and registrars in protecting your brand and online presence against emerging threats.

Feature "Cybersecurity"
SIWECOS - Secure Websites and Content Management Systems
While content management systems regularly release security updates, end users often seem disinclined to use them. David Jardin, founder and Chief Executive Officer of djumla, looks at the implications of this behavior and explains how the SIWECOS service can help web hosters to protect against cyber attacks.

Feature "Cybersecurity"
Telling the Good Guys from the Spammers - It's Like a War Out There
During the 2017 CSA Summit in Cologne, Oath’s Marcel Becker talked to eco’s Rosa Hafezi about what good senders can do to stand out in a sea of spammers, and how the email community needs to work together to beat the bad guys.

Feature "Digital Infrastructure"
Cyber-Resilience – A Major Challenge for the 21st Century
Our dependence on the digital world requires a behavioral change to increase not only security, but also resilience through anticipating threats. Yves Reding from EBRC explains the concept of “cyber-resilience” and its impact on business continuity.

Feature "Self-regulation"
Bringing Order to the Digital Wild West from the Bottom Up
The strongest argument in favor of bottom-up, multi-stakeholder governance is that it actually works. Vittorio Bertola from Open-Xchange explores why self-regulation of the Internet is better than the alternatives

Feature "Cybersecurity"
Not in Our Domain: How EURid is Using AI and Global Cooperation to Tackle Cybercrime
EURid takes an innovative approach to help outwit cybercriminals, including helping to identify potentially malicious registrations at source.

Feature "Cybersecurity"
Whatever, put a chip in it
The careless days in IoT are numbered: Sebastian Floss explores the value of Security by Design for IoT devices, and offers 4 simple rules to get started.

Feature "Domains"
Investigating Web Data for Brand Protection Purposes
Alona Borzhemska and Volodymyr Holovash from DomainCrawler on how brand owners can adopt proven best practices to fight online counterfeit sales.

Feature "Cybersecurity"
Working Securely at Home – 9 Tips for Company Security
Daniel Heck from Rohde & Schwarz Cybersecurity offers work-from-home tips to increase the IT security of your employees.

Feature "Email"
Bringing Email Security into the Mainstream: A Call to Action for Companies
In the face of escalating cyber threats, email security is emerging as a crucial battleground for businesses of all sizes. The eco Association’s Michael Weirich urges companies to elevate their defenses and explains how they can fortify their digital communications against increasingly sophisticated attacks.

Feature "Artificial Intelligence"
AI to Detect and Defend Against Cyber Attacks
Marc Wilczek from Link11 speaks to dotmagazine about the power of AI to solve cyber security issues.

Feature "DDoS"
Two Sides of DDoS Attacks: The Largest Attack of All Time and Focus on SMEs
Even though we recently experienced the largest DDoS attack of all time: With Denial-of-Service attacks, it is no longer just a question of bringing down the websites and online shops of large companies. Now, small and medium sized enterprises (SMEs) also need protection, according to Niko Bender from PlusServer.

Feature "Email"
The Challenges of Fighting Phishing
Terry Zink, Program Manager at Microsoft, talked to eco’s Rosa Hafezi during the 2017 CSA Summit about getting phishers off your network and keeping them off.

Feature "Cybersecurity"
Smart Contract Security – Expect and Deal with Attacks
In a world where smart contracts are executed by a network of mutually distrusting nodes without a central authoritative entity, security plays a pivotal role. However, security matters are often neglected – with dire consequences, as Dr. André Kudra points out.

Feature "Cybersecurity"
Cyber Security & Data Protection in Japan
In Japan as elsewhere, the attack behavior is becoming more sophisticated: Professor Koji Nakao, an eminent Japanese IT security specialist, talks to dotmagazine about differences and similarities in cyber security trends, and about how we need to collaborate to present a counter-measure to cyber threats.

Feature "Encryption"
Industry 4.0: The Authentication of Things within the Internet of Things – PKI as a Solution Approach
Klaus M. Brisch, LL.M. and Marco Müller-ter Jung, LL.M., from DWF Germany, shed light on the question whether a Public Key Infrastructure (PKI) in compliance with the security infrastructure implemented by the electronic signature legislation is suitable to establish a secure authentication within the Internet of Things. Numerous applications depend on the communication between different devices and their ability to interact with each other.

Feature "Blockchain"
Blockchain-based Solutions and IT/Cyber Security for Autonomous Driving – Legal Barriers
The great complexity of the technical processes used in connected and autonomous cars leads to complex legal requirements. Two attorneys-at-law from DWF Germany, Klaus M. Brisch and Marco Müller-ter Jung, explore the raft of associated implications – spanning contract and liability issues to issues of IT and data security – and conclude that legal innovations at European level might enhance further technical progress.

Feature "Cybersecurity"
Sanitizing Files to Prevent the Spread of Malware
Omri Eytan from odix explains how content disarm and reconstruct (CDR) technology can prevent malicious code hidden in files from entering company systems.

Feature "Cybersecurity"
Bringing Together Safety and Security to Protect the Physical World
Gordon Muehl, Global CTO Cybersecurity and Privacy Protection at HUAWEI, on protecting against industrialized cyber crime and making security technology easier to use.

Feature "Domains"
Congratulations on Your New Business – We Need to Talk
Kelly Hardy from CentralNic provides cybercrime advice for end customers and clients operating businesses online during the pandemic boom.

Feature "Cloud Computing"
Cloud Access: Resist Naive Assumptions
Süleyman Karaman, Managing Director of COLT Technology Services, on secure cloud access, dedicated leased lines, and a small village in Bavaria.

Feature "Cybersecurity"
Prevention, Defense, and Detection: IT Security in Companies
With increasingly sophisticated and personalized attacks on company IT, companies need to develop new ways of dealing with IT security risks. Prevention is no longer enough, according to Nikolei Steinhage from Fidelis.

Feature "Cybersecurity"
Detecting and Defending Against Cyber Threats – Staying One Step Ahead with the Connectivity Cloud
Dominic Haussmannn from Cloudflare reveals how the Connectivity Cloud is revolutionizing cyber defense, helping companies outpace evolving threats and safeguard critical infrastructures.

Feature "Industrial IoT"
3D Printing: Rights to Data and IT Security in the Field of Additive Manufacturing
An exploration of the legal implications of copyright law for industrial 3D printing, and of the importance of IT security for Additive Manufacturing, by Klaus M. Brisch, LL.M. and Marco Müller-ter Jung, LL.M., DWF Germany

Feature "Cybersecurity"
Attacks On Corporate Cloud Accounts as Companies Work From Home
A new research study by cyber security specialist McAfee reports on online behavior and cyber security trends during the COVID-19 crisis.

Feature "Cybersecurity"
Cyber Security: Dancing with Wolves
Independent consultant Gerd Simon offers advice for companies on improving IT security and undertaking an effective risk assessment for cyber security.

Feature "DDoS"
The Dangers of DDoS Overconfidence
Chris Townsley, EMEA Director at CDNetworks, discusses the rising threat of DDoS attacks, and the misplaced confidence of European businesses in their ability to overcome cyber attacks.

Feature "Cybersecurity"
Securing Smart Contracts
Smart contracts, based on blockchain technology, are software programs that offer a very secure and transparent way of documenting and automating business processes. But as software programs, they are not immune to security vulnerabilities, as Professor Alexandra Dmitrienko explains.

Feature "Cybersecurity"
New Frontiers for Car Security: API Management
When it comes to driverless cars, most of the talk is about high-precision sensors and AI. But a host of other enabling IT services bring their own risks. Marco Comastri of CA Technologies argues for the need for a paradigm shift among OEMs: one that would make cyber and network security as much of a core competence as engine control, airbags, or brakes.

Feature "Cybersecurity"
Artificial Intelligence in Cyber Security
Nils Kammann, Solutions Architect at Xantaro, on the hype of artificial intelligence in cyber security, an essential delineation of terminology, the challenges we face, and the need and chance for new security models.

Feature "Cybersecurity"
IT Security: Don’t Try to Make the Impossible Possible
IT security is a major cause for concern for companies, and it is important to ensure a good level of security to protect against hacker attacks and industrial espionage. But should companies aim for perfect security? This is not sensible, Karsten Nohl from Security Research Labs tells dotmagazine.
Industry Insights "Cybersecurity"
Secure SD-WAN – Helping CIOs Meet their Goals
Prevention, Defense, and Detection: IT Security in Companies

Feature "Authentication"
DMARC is Here to Stay. Now What?
Alex Brotman, Comcast, and Patrick Koetter, sys4 AG, on how DMARC (Domain-based Message Authentication, Reporting, and Conformance) can help companies to protect their customers and their brands from abuse.

Feature "Industrial IoT"
Industry 4.0: Rising to the Cybersecurity Challenge in Smart Manufacturing
The article discusses the smart manufacturing sector by highlighting its characteristics and illustrating what the main challenges are for enterprises in the sector, and how TANGO project proposes a solution to mitigate cybersecurity risks through a dedicated case study.

Feature "Cloud Computing"
Cloud Native Security: Security from the Start
Sylvia Lösel from IT-Business Magazine interviews Sebastian Schäffer, Alice&Bob.Company, on Security as Code and getting security right from the start.

Feature "Cybersecurity"
Targeted Phishing Emails to Train IT Security Awareness
It used to be thought that IT security could be solved purely with technical solutions, but now it seems that the human element has become much more important. dotmagazine spoke to David Kelm, CEO of IT-Seal, to find out how they use machine learning as a means to train staff in secure online behavior.

Feature "Digital Ecosystem"
From Discovery to Defense: Mastering API Security in Modern Digital Ecosystems
Lisa Fröhlich, Corporate Communications at Link11, dives into the critical importance of API security, outlines common threats, and shares actionable best practices to protect sensitive data and ensure business continuity.

Feature "Company Security"
Proactive Hunting for Hidden Threats using Metadata
Andrew Bushby from Fidelis Cybersecurity explains how metadata can be used to aid forensic investigations when a company discovers it is under attack

Feature "Cybersecurity"
Security and E-Health: Between Privacy and Beneficial Innovation
Maik Morgenstern, CTO at AV-Test, offers advice on what to look for in e-health gadgets and services in order to benefit from innovations without giving away too much sensitive data.

Feature "Cybersecurity"
SHIELD: An Open Platform for Secure Digital Identities
For digitalization to progress, there is need for reliable and secure identification: Michaela Templin from the eco Association reports on the progress of one digital ID project.

Feature "Cybersecurity"
Fundamentally Preventing Attacks - In & Out of the Cloud
Considering the steadily rising number and growing scope of cyber attacks, companies' IT security needs a significant upgrade. A talk with Daniel Heck, Head of Marketing at Rohde & Schwarz Cybersecurity, about long-term defensive strategies, and data protection in the cloud.

Feature "Cybersecurity"
Radio Equipment Directive: New Cybersecurity Requirements for IoT
The EU is tightening IoT security standards. Eric Clausing, Lead IoT at AV-TEST looks at what this means for manufacturers, small businesses, and consumers.

Feature "Domains"
Where Domain Security Meets the Supply Chain Crunch
Sue Watts from CSC, on how to prevent fraud related to fake domain registrations from capitalizing on global and societal events.

Feature "DNS"
DNS Cookies: The Transaction Mechanism to Protect the Namespace
Although they are not the cure for all name server problems, DNS cookies offer an extra layer of protection and are particularly effective against off-path attacks. Simone Catania, InterNetX, looks at how DNS cookies can make DNS transactions more secure.

Feature "Company Security"
“Phishing” Your Staff to Raise Security Awareness
Do you want to improve IT security in your company? The number one task is to train your staff in security awareness on a regular basis, according to Dr. Niklas Hellemann from SoSafe Cyber Security Awareness.

Feature "Cloud Computing"
Data Protection in the Age of Digitalization - An Opportunity for Europe or an Offside Trap?
The fine line between protection and incapacitating society: Andreas Weiss, Director of EuroCloud Deutschland, looks at the ongoing debate on data protection and data security, cloud computing, and the impact of digitalization – and when too much defense hampers success.

Feature "IoT"
The Internet of Things – Understanding IoT from a Security Perspective
Joseph Carson from Thycotic looks at IoT risk assessment and calls for a redefinition of IoT to achieve clarity from a security perspective.
Industry Insights "IoT"
Making the Internet of Things More Secure

Feature "E-Health"
Cybersecurity in the Hospital Environment – How can Hospitals Protect Themselves from Hacker Attacks?
Tatjana Hein from the eco Association reports on a cyber-crime prevention expert’s advice for protecting hospitals against cyber attacks.

Feature "Cybersecurity"
Securing Industrial IoT – Business Continuity for Connected Production Plants
What are the security risks of introducing IoT into production plants? What should companies do to mitigate such risks? Wolfgang Strasser, CEO of @Yet, talks to dotmagazine about securing IoT plants and products, and what to do in the event of a cyber attack.

Feature "IoT"
Making the Internet of Things More Secure
Klaus J. Müller from LEITWERK explains how IoT can be made more secure – by removing the end-user’s ability to make bad decisions.

Feature "Security"
The Sectors at Risk from DDoS and Bot Attacks: How to Stop them
Andrew Slastenov from Gcore, on the risks of DDoS and bots and how to protect company systems and networks.

Feature "Email"
Secure Email Communication
In today’s digital age, ensuring the security of email communication is paramount. Learn about the comprehensive Technical Guidelines from the German Federal Office for Information Security (BSI), authored by Kristina Pohl.

Feature "Cybersecurity"
360 Degree Security: Why Do We Need to Look Beyond Just Cybersecurity?
Security today goes far beyond just cybersecurity, as Thomas Tschersich from Telekom Security emphasized at eco’s Internet Security Days. He highlights the need for a 360-degree approach that addresses cyber threats, workforce challenges, geopolitical risks, and supply chain vulnerabilities.
Industry Insights "Cybersecurity"
The Hidden Trap of Vendor Lock-in: How MSPs Can Escape With Hybrid IT
Brand Abuse: How to Detect Threats Before Your Customers Do

Feature "Cybersecurity"
Improving Cyber Resilience Worldwide
Silvio Oertli from Switch-CERT reflects on the importance of shared knowledge & trust-building mechanisms in incident response amidst commonplace cyber threats.

Feature "Email"
Enhancing Email Security: A Collective Responsibility
Claudia Plattner, President of the BSI, calls for collective action in enhancing email security amidst growing cyber threats. As outdated email systems continue to expose vulnerabilities, the tools to strengthen our digital communications are already within reach – it's time to put them to use.

Feature "Encryption"
Encryption – Balancing Needs for IT Security & Law Enforcement
Klaus Landefeld, eco Vice-Chair, looks at ways to enable access to digital evidence internationally, without dismantling security and trust on the Internet.

Feature "Company Security"
IT Security: People Still Don’t Seem to Realize that the Threats Affect Them
The eco Association has just published its annual IT security study. Oliver Dehning, CEO of HornetSecurity and Leader of the eco Competence Group Security, offers his perspective on the results.

Feature "DNS"
A Day in the Life of a Man with a Key to the Internet
dotmagazine’s Judith Ellis talks to Olaf Kolkman of the Internet Society about the Domain Name System and his key to the Internet.

Feature "Cybersecurity"
Fake Shops: Tips for Safe Xmas Shopping
Fake Internet sales platforms are popping up all over the place in December, the strongest month for online sales. Peter Meyer, Head of Cyber Security Services at eco, provides advice on how consumers can recognize fake shops and avoid the heartache of being ripped off this Christmas.
Industry Insights "Cybersecurity"
SIWECOS - Secure Websites and Content Management Systems

Feature "Company Security"
How Much of an IT Security Risk Are You to Your Company?
The best security is only as strong as its worst password and naivest user. Markus Schaffrin from the eco Association explains how important the behavior of staff and management is for company security.
Industry Insights "Company Security"
“Phishing” Your Staff to Raise Security Awareness

Feature "Cybersecurity"
Shouldering Responsibility for IT Security – A Multi-Stakeholder Approach
IT security is the mutual responsibility of all stakeholders, from civil society to industry and government, says Prof. Norbert Pohlmann
Industry Insights "Cybersecurity"
Improving the Security and Resilience of the Internet through MANRS

Feature "Cybersecurity"
Hand in Hand for Secure Websites – Making the Internet Safer
Open source CMS communities like TYPO3 are working with the eco Association to improve security for commercial and private websites, reports Markus Schaffrin from eco.
Industry Insights "Cybersecurity"
Women in Digital Ecosystems
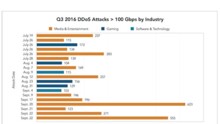
Feature "DDoS"
Optimal Protection against Cyber Attacks
Manfred Fochler from Akamai explores the impact of DDoS attacks, and describes a mitigation case study of the football team FC Bayern Munich

Feature "Security"
Cyber Security in the EU
First EU-wide cyber security rules established - What's new for European companies? Interview with Thorsten Ihler from Fieldfisher

Feature "DNS"
Next Steps in Combatting DNS Abuse
Thomas Rickert and Lars Steffen from the eco Association take stock and give an outlook on collaborating in the fight against abuse involving the DNS.

Feature "Company Security"
Why IT Security is Like Shopping for Christmas
There are three striking similarities between IT security and shopping for Christmas. Most of us have too much stuff to begin with. Also, there is too much theatre involved. And finally, socks. You can enjoy a holiday season without worries if you keep these things in mind.
Industry Insights "Company Security"
The Dangers of DDoS Overconfidence
Cyber Security & Data Protection in Japan
The Human Element of IT Security

Feature "Cybersecurity"
Building Trustworthiness and Acceptance of IT Security Solutions
How can companies create trust in IT security solutions? Through trustworthiness, argue Prof. Norbert Pohlmann from eco & Ulla Coester from xethix Empowerment.
Industry Insights "Cybersecurity"
The Shared Responsibility Model – an Important Basis of Cloud Security
DNS Abuse: Everyone’s Problem

Feature "Company Security"
Cyber Crime Against Companies – There’s Money to be Made
Security specialist Oliver Dehning from Hornetsecurity talks about protecting companies from cyber crime, encryption, and not throwing out the baby with the bathwater.

Feature "Cybersecurity"
Current Challenges in EU Telecom Security
What is the current state of security for telecommunications in Europe and what are the challenges telecom companies are facing to keep our communication secure? Dr Dan Tofan, from the EU Cyber Security Agency, ENISA, gives insight into the challenges.
Industry Insights "Cybersecurity"
Reestablishing communications when disaster strikes
Bridging the Digital Divide

Feature "Cybersecurity"
Security Risk Analysis and AI Support
Sebastian Kurowski from the Fraunhofer Institute for Industrial Engineering looks at how artificial intelligence can be used to optimize IT security risk analysis in companies, offering relevant support for ITR specialists and for strategic decision-making.
Industry Insights "Cybersecurity"
Targeted Phishing Emails to Train IT Security Awareness

Feature "Self-regulation"
Online Reputation and Abuse – Interconnected Problems?
Wido Potters from BIT BV explores the advantages of fighting Internet abuse together with the support of AbuseIO – a self-regulatory approach to Internet abuse

Feature "Authentication"
Adding Trust & Security to Internet Interactions with DNSSEC
DNSSEC does two things: It ensures you’re talking to the right online resource, and it verifies that the information you receive has not been tampered with, Patrick Koetter from sys4 AG explains.

Feature "DNS"
The Domain Name System - Making a Company Website Findable
Sven-Holger Wabnitz explains how DNS works and how important it is for findability and brand identity in the Internet

Feature "Artificial Intelligence"
Artificial Intelligence and IT Security - More Security, More Threats
Prof. Norbert Pohlmann from eco investigates the dual role of AI as both a powerful security asset and a potential attack vector. He highlights the importance of securing AI systems while underscoring the need for human oversight in critical areas to ensure safety and trust.
Industry Insights "Artificial Intelligence"
Maintain Connectivity and Security for AI-Based Apps

Feature "Cybersecurity"
Connected Car Security
The potential for the connected car to improve safety on the road is immense, but its ability to do so also depends on the IT security built into the system. dotmagazine spoke to IT security specialist and Member of the Board at the eco Association, Professor Norbert Pohlmann, about the challenges of securing connected cars.
Industry Insights "Cybersecurity"
New Frontiers for Car Security: API Management
Blockchain-based Solutions and IT/Cyber Security for Autonomous Driving – Legal Barriers

Feature "Blockchain"
What Can Blockchain Do For You?
“The Internet never forgets!” Although untrue, this statement reminds people to think twice before putting information online – and out of their control. The advent of blockchain changes everything. Blockchain forgets nothing – and it brings back content control. Mathias Röckel looks at the potential of this new technology for innovative commercial enterprise, as well as for Internet infrastructure providers.

Feature "Cybersecurity"
Ransomware Has Not Just Been Around Since Yesterday
Michael Weirich from the eco Association, on the impact of ransomware on companies and the need for a contingency plan.
Industry Insights "Cybersecurity"
The Sectors at Risk from DDoS and Bot Attacks: How to Stop them

Feature "Quantum Computing"
A Quantum-Safe Future
An interview with Dr. Joachim Schäfer from IBM on quantum computers, the quantum advantage and quantum-safe encryption.

Feature "Cybersecurity"
How Far Should the State Be Allowed to Go for the Purposes of Digital Security?
Klaus Landefeld on responsibility for IT security and how combatting crime has paradoxically become one of the greatest threats to security in cyber space.

Feature "Cybersecurity"
Making Connected Cars Safe
Prof. Norbert Pohlmann from the eco Association looks at how the automotive Internet industries should work together to improve Connected Car security.
Industry Insights "Cybersecurity"
Data Protection for Connected and Autonomous Vehicles

Feature "Brands"
Preventing Counterfeiting and IP Abuse with Customer Engagement
Companies ignore brand protection and the problem of counterfeiting at their own and their customers’ risk, explains Stuart Fuller from CentralNic.
Industry Insights "Brands"
Boost Your Brand and Raise the Bar for Fraud – the Benefits of a dotBRAND
Mitigating Risks for Brands with Smart Domain Management Tactics and Tools
The Importance of a Domain Name and a Trademark to Protect your European Brand
Founder spotlight: Unique Ideas with Creative Domains

Feature "Industrial IoT"
Driving Digital Transformation
Forecasts of social disintegration and wide-spread unemployment caused by Industrial IoT are a melodramatic overreaction stemming from the fear of change. To the horseshoe smithy, the car also posed an existential threat – but does that mean we should return to the dark ages? Judith Ellis explores the attitudes to digital transformation, the challenges from smaller companies, and the steps needed to make it a success.

Feature "Cybersecurity"
Trust & Security in the Blockchain
The early use cases for blockchain technology centered around cryptocurrencies. But the same processes that secure Bitcoin and friends can also be used for securing other forms of data, for example in administration. So, what is it that makes blockchain so secure? Professor Norbert Pohlmann, from the eco Association, explains.
Industry Insights "Cybersecurity"
Securing Smart Contracts
Smart Contract Security – Expect and Deal with Attacks

Feature "Blockchain"
doteditorial: Blockchain & E-Government – Giving Citizens Control of Their Data
E-Government is a major driver of blockchain technology. Stephan Zimprich from fieldfisher looks at how the transparency and immutability of blockchain can help give citizens digital self-determination.
Industry Insights "Blockchain"
Blockchain for Education: Lifelong Learning Passport
Blockchain Technology: A Must for Modern and Forward-Looking IT

Feature "GDPR"
Collaboration across the Atlantic: Data Protection & Internet Policy
Many American companies are still unaware of how the new EU General Data Protection Regulation will affect them. Data protection gurus Thomas Rickert from the eco Association & Christian Dawson from i2Coalition look at how two voices for the Internet are teaming up on GDPR, ICANN, and beyond to ensure that the Internet and the organizations that build it have a voice on both sides of the Atlantic.

Feature "Email Marketing"
doteditorial August 2017
“The Future of Email”, the August 2017 issue of dotmagazine, explores where this essential medium is heading and what its potential is, focusing on email marketing and how to make sure that relevant marketing messages truly reach target customers, and how to beat the email bad guys.

Feature "Cybersecurity"
The Cyber Resilience Act and its Impact on Security in the IoT
The EU’s Cyber Resilience Act will strengthen cybersecurity rules for hardware and software products. Tatjana Hein, eco Association, looks at what IoT manufacturers can expect.
Industry Insights "Cybersecurity"
Improving Cyber Resilience Worldwide

Feature "Smart City"
Cybersecurity is a Key Driver of Smart City Markets
Markus Schaffrin from the eco Association looks at the fundamental importance of security to the success of Smart City projects.
Industry Insights "Smart City"
Remote Work Spells Opportunity for Service Providers
Working Securely at Home – 9 Tips for Company Security
AI and Cybersecurity – What to Expect and How to Protect your Organization
Fortifying Cyberspace: How Innovative Companies from Canada’s Ontario are Protecting Us Against Cyber Attacks

Feature "Cybersecurity"
The Current Situation of IoT Security and What to Do
Hardly any IT market sector in recent years has experienced growth rates like those in IoT, but securing networked devices and IoT structures still lags behind, explains Olaf Pursche from the AV-Test Institute.

Feature "Data Protection & Privacy"
doteditorial December 2017
This festive season, dotmagazine examines what’s involved in keeping your most valuable business assets – your ID, your finances, customer data, and your reputation – safe and secure.

