Building Trustworthiness and Acceptance of IT Security Solutions
How can companies create trust in IT security solutions? Through trustworthiness, argue Prof. Norbert Pohlmann from eco & Ulla Coester from xethix Empowerment.

©Fokusiert| istockphoto.com
In Part I of this set of articles by Prof. Norbert Pohlmann from the eco Association and Ulla Coester from xethix Empowerment, the authors argue that the model of trustworthiness provides a framework for developing strategies to engender trust for their company and their IT-solutions. In the following article, the authors continue by determining the factors and action points needed to engender trust for the given IT-solution and for the company.
The structure of the model of trustworthiness
The relationships for building trust are shown in the model of trustworthiness (Fig. 1) and are explained below on the basis of the individual factors.
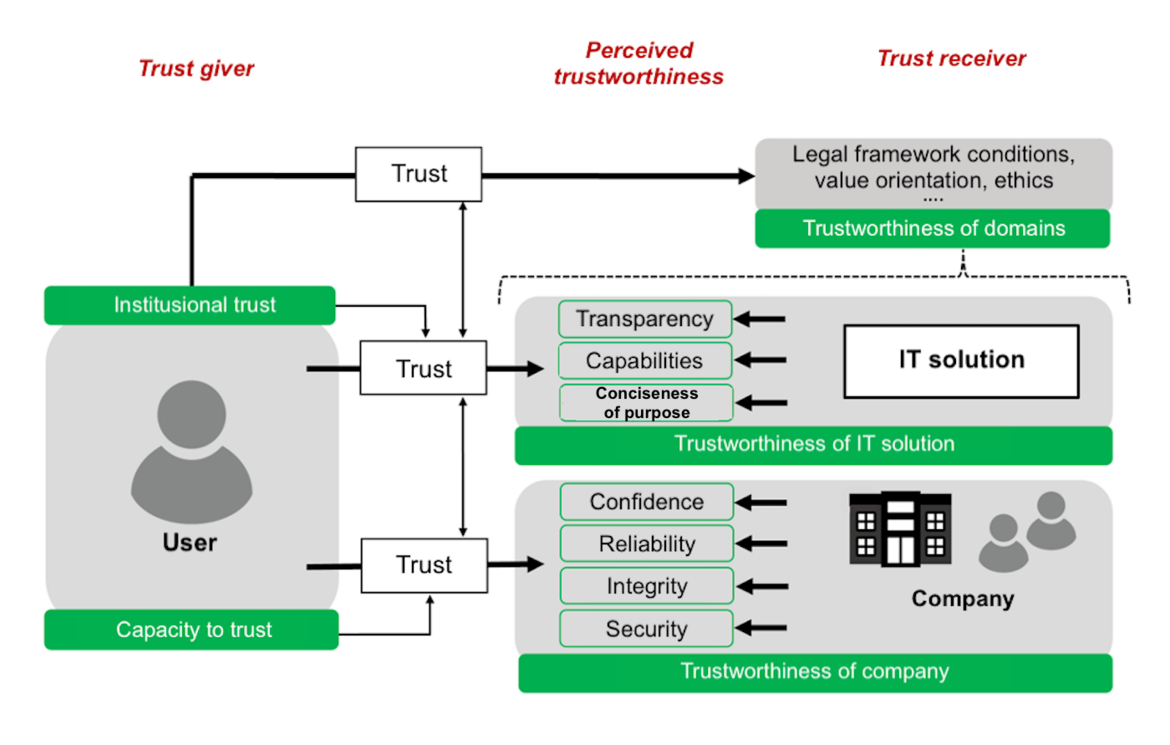
Fig. 1: Model of Trustworthiness
For a manufacturer to be able to transfer this trust to its IT solution in a dedicated manner, other factors alongside cybersecurity also play a relevant role in terms of perceived trustworthiness: Transparency, performance, and having ‘conciseness of purpose’. Only through the presentation of all aspects will the user be able to develop trust in the IT solutions offered.
Factor: Transparency of an IT solution
The principal benefit of the decision to be transparent is that it shows how the company takes the needs of its users seriously and is prepared to communicate openly. By no means does this involve having to disclose every detail of the IT solution or all of the associated business activities. Rather, it means that all relevant information is provided that a user needs to make a valid decision about the trustworthiness of the IT solution in the given context. Overall, the quality of information thus plays a decisive role – it should be participatory and particularly balanced, meaning it should take the interests of all parties equally into account.
In the past, this form of communication was not necessary. However, due to the now high degree of complexity involved, it is essential to act in this way in order to increase the willingness to have this solution used. This demonstrates the interplay between trust and trustworthiness: A company depends on the acceptance of its users. On the other hand, due to increasingly intelligent attacks and more complex cybersecurity mechanisms, it is becoming more and more important for users to ensure that their cybersecurity needs are also adequately met by the IT solution.
Package insert on cybersecurity: For example, one way to ensure transparency is to provide a package insert describing how cybersecurity mechanisms in the IT solution will be used to ensure a reduced risk of the various attacks. It is also important to show what residual risks exist, how the user can deal with them, and how the company can provide support.
Presentation of certificates: Another important aspect of transparency is the availability of existing certificates and the associated reports that are available for the IT solution. This enables the user to determine which aspects have been analyzed by cyber security experts from the certification bodies.
Factor: Capabilities of an IT solution
The capabilities of an IT solution are what the user can immediately comprehend and also control. Therefore, the measurable criteria for the user’s evaluation of the solution result from the extent to which users feel supported in achieving their intended purpose, and how well suited the IT solution actually is in this regard. Reliability and predictability are among the evaluation criteria to be mentioned here. It is also highly relevant that the company’s competence is reflected when it comes to the capabilities of the IT solution. After all, a lack of capabilities ultimately results from errors in the areas of competence or strategy. This therefore shows both the connection and interplay between the trustworthiness of the IT solution and the company.
Among other things, the usability or the performance of the cybersecurity mechanisms can serve as a baseline for the user’s evaluation.
Usability: The extent to which cybersecurity mechanisms and management can be operated easily or even intuitively by the user.
Performance of cybersecurity mechanisms: The extent to which the performance of the IT solution decreases, for example through the encryption of the data. Or the length of time an attack detection system takes from detecting an attack to responding, for example, by sending an alert or an automatic response.
Factor: Conciseness of purpose of an IT solution
Whether or not a solution has a conciseness of purpose manifests itself in the intended use of the IT solution. For companies, this means that the function and intention of the IT solution are precisely defined during development. As a result, the intended use of the IT solution should be clearly evident to the user. For this reason, it is important to ensure that the purpose of the IT solution can be easily and immediately comprehended – including through the use of characteristic features. Conversely, however, this by no means suggests that a low level of functionality must go hand in hand with having a conciseness of purpose. Furthermore, it is necessary to openly present any relevant change or extension to the IT solution – especially if this means that the originally intended use is no longer clearly discernible.
If, in addition to the actual application, an IT solution offers further functions that are only in the interests of the company or third parties, these must also be clearly presented and described. Examples include:
Disclosure of the business model: If sensitive user data is collected with the help of the ‘pay with personal data’ business model and used for individualized advertising and/or sold at profit to third parties, this must be clearly communicated.
Provision of insight into new features: For example, Apple’s new detection system, which is designed to indiscriminately scan all data on iPhones for child pornography, has a high social value but poses a risk to users in terms of their privacy – simply given the fact that the search takes place on the end device. Since it is also possible in principle to arbitrarily search for other content, this can pose a real endangerment to certain groups (in some countries). Serious deviations from the solution’s conciseness of purpose must be made immediately transparent for the user. This is essential so that the user can come to an informed decision for or against future use.
The trustworthiness of companies
When deciding to use new IT technologies, aspects of the respective IT solution are not the only decisive factors. On the contrary: the company’s reputation also plays an important role here. Since it is currently apparent that trust in IT technologies, applications, and services is in principle not (yet) fully justified, it is necessary for companies to fulfill additional conditions in order to increase their level of trustworthiness. To this end, both manufacturers and service providers must make their strategy visible to the outside world.
In implementation, this means aligning their actions with the defined criteria of trust, reliability, integrity, and security. The decisive factor for the definition is that it is possible to rationally assess the company-specific trustworthiness, in order to make it possible for the user to evaluate the corresponding parameters quickly and easily.
Factor: Confidence in a company
Confidence is a relevant criterion for trustworthiness. Generally, with regards to functionality, this can be generated by companies having both the capability and the means to provide not only reliable but also secure technology, services, and applications.
It is important to develop a strategy to fulfill this criterion and to document it in a trust guideline. For this purpose, among others, a concept must be created that concerns the parameters which must be fulfilled. In this context, by way of example, the following factors are then of high relevance:
Employees: Parameters for the training, qualification, and professional development of employees: Whether the employees completed a course of study with a focus on IT security or have undergone appropriate further training, what experience they have in this area, and what additional qualifications they have, such as CISSP or the German T.I.S.P. [1].
Quality standards: Parameters for development and production: Description of the development process, definition of the accompanying quality assurance, including implementation and specification of the life cycle management.
Operating resources: Parameters on the quality and quantity of software and hardware: Description of the standards that must be met in order for the IT systems used for business activities (and especially for development) to meet all requirements, designation of quality criteria.
Factor: Reliability of the company
Reliability means that IT technologies and IT solutions only execute the processes that users want or expect, and that they do so with as close to 100% reliability as possible. Reliability thus implies that companies are fundamentally benevolent. This means that they act in the best interests of their users, i.e. they focus on their users’ needs rather than particularly focusing on their own company interests. An example of this is that they do not instrumentalize obvious weaknesses of their users in order to gain a (financial) advantage, and thus refrain from causing them harm. Such instrumentalization could take the form of exploiting how special offers can entice customers: Users would then regularly be offered outdated stocks of anti-malware products – which no longer meet the state of the art and therefore do not offer adequate protection against current attacks – at a heavily discounted price just to get rid of them or simply to make money.
However, given that no company is perfect, reliability also requires the willingness to continue developing. In order to compensate for deficits that still exist at present, manufacturers must therefore integrate mechanisms by means of which they can proactively optimize the degree of their reliability on an ongoing basis and then appropriately present these development steps. An ideal state is achieved when user confidence is congruent with the actual reliability of the company or the IT solution. Conversely, this means that companies risk their trustworthiness or lose it completely if their actions do not conform with their external image.
How will companies have to act here in the future? What should be included in their reliability management? The following are some of the factors that are of relevance in this regard:
Act cooperatively in order to more effectively identify the real needs of the user and to provide individual support to the user when problems arise. Assuming overall responsibility in the event of damage or undertaking recalls in the event of identified problems are examples of cooperative action. This means that manufacturers must inform their users immediately – if possible, by direct means – when serious vulnerabilities are identified. If this information is initially published by other sources, for example via social media or the trade press, this reduces the trustworthiness of the manufacturers.
Act responsibly in order to create added value for users through the correct use of functions which are to the users’ advantage. Responsible action also includes reviewing and continuously monitoring the supply chains on the basis of a wide variety of factors, and taking all measures to prevent fraud. This means, for example, that manufacturers must do everything possible to prevent supply chain attacks; for instance, by reviewing suppliers and/or examining the content and the software of the respective supplier. Especially in this context, but also in comparable constellations, trustworthiness can only be built up by assuming overall responsibility.
Factor: Integrity of the company
Integrity is demonstrated through manufacturers and service providers taking into account all the factors that are relevant to trustworthiness, paying particular attention to the ethical dimensions. This means that a manufacturer, as a trust receiver, is in principle in the position to keep all the promises it has made – and does actually keep them – as well as being generally prepared to take account of both the norms and values of society.
The ethical orientation of companies, in particular, will come under even greater scrutiny in the future. This is demonstrated by various studies: for example, by the finding that 93 percent of users in Germany demand an ethically acceptable use of IT technology. Therefore, integrity should be seen as a must in all business activities. A one-dimensional, purely technically-oriented mindset that does not take ethical aspects and values into consideration will become less and less profitable – or even only profitable in the short term. This comes down to the volatility of user behavior, which can be rapidly influenced by negative events or posts. What is also important to consider in this context is the fact that the potential for trust varies from user to user, and that the basic attitude is therefore relatively difficult to calculate.
Therefore, one of the most important steps for companies to take is to draft an integrity maxim with a clear affirmation of their business model and of company-specific factors. Without question, this includes clearly addressing the ethical requirements. Some ethical requirements are presented below as examples:
Privacy protection: This requirement includes, on the one hand, good handling of customer data, such as immediate deletion when it is no longer needed, and protecting this data through encryption. In addition, it concerns the commitment not to exploit users’ data for further commercial purposes.
Accountability: One of the key aspects that accountability addresses is ensuring the verifiability of the quality of IT solutions. In addition, it should be mandatory for companies to review the technologies they use, and disclose any corresponding negative effects on society.
No limited cybersecurity: Manufacturers and providers must commit to ensuring that the cybersecurity mechanisms used do not employ any weakened ciphers, random number generators, or other cryptography, and that they do employ secure keys. Likewise, it is also necessary to ensure that no backdoors are built into cybersecurity solutions. In presenting this to the user, manufacturers can make this claim with the aid of a trust mark, one example being ‘IT Security made in Germany’ [2].
Factor: Security of the company
Recognizing the importance of cybersecurity and implementing it ensures that technologies – that is, services and applications – can be used on the Internet at low risk. However, today this aspiration remains fiction (as yet), given that ransomware, DDoS, and phishing attacks, among others, are commonplace. Services used on a daily basis, such as email programs, online banking, and online stores, do not offer the level of trustworthiness required to securely handle critical business processes.
Companies therefore need an adequate and well-defined IT security policy to ensure the best possible protection for their customers. As users are generally not in a position to protect themselves adequately, a continuous process of implementation of the current security requirements is necessary. Among others, the following factors are highly relevant in the context of security:
Presentation of cybersecurity measures used: In this field, manufacturers should demonstrate what they are doing to protect both the IT solution and their own company, respectively, from cybersecurity risks. Unlike the “package insert on cybersecurity”, descriptions and background information can be more detailed in this case.
Certification of the IT solution: Certification of the quality and trustworthiness of IT solutions must be carried out by qualified independent organizations that review and test according to defined criteria. Criteria arise, for example, from the areas of IT security, data protection, and the development and quality assurance processes. The certification of the IT solution, but also of the company, is an important measure to build trust.
Regular review of the products and the company: The goal here is to actively and continuously identify vulnerabilities with the help of penetration tests and Red Teams, so that security vulnerabilities can be eliminated as quickly as possible through updates – and thus not used for attacks. This applies both to the IT solutions offered and to the companies and their suppliers. This makes it possible to achieve a high level of security – verifiable for the user at all times – in the ongoing development process.
Bug bounty program: The central idea of bug bounty programs is to use financial incentives to encourage the hacker community, scientists, and other stakeholders to find vulnerabilities in the IT solutions of the respective companies. This makes it possible to fix vulnerabilities as rapidly as possible, preferably before criminal organizations can exploit them.
Cybersecurity strategy: A cybersecurity strategy is a longer-term, planned approach aimed at minimizing the existing risks of attack on the company’s digital assets. Since the presentation of this increases the trustworthiness of a company, the fundamental strategy should also be communicated externally.
Conclusion
The Model of Trustworthiness as applied to the development of trust in IT solutions and the associated companies demonstrates clearly the levels at which companies are able to directly increase their perceived trustworthiness through appropriate action and the provision of information. Put simply, the higher the trustworthiness of the company – which implicitly means that all aspects of trustworthiness are also implemented for the company’s IT solutions – the more likely it is for users to be willing or able to place their trust in the company. This is important, especially with regard to IT solutions, as this can increase the acceptance amongst users.
This not only sounds logical in theory, but is also easily implementable. Therefore, it is necessary for companies to take an in-depth look at the “Model of Trustworthiness”.
As founder/CEO of the company xethix Empowerment, Ulla Coester advises on Corporate Digital Responsibility processes, with a focus on trustworthiness/digital ethics. She is also a lecturer in Digital Ethics (Fresenius University of Applied Sciences, Cologne) and a member of the Standardization Evaluation Group 10/IEC: Ethics in Autonomous and Artificial Intelligence Application.
Norbert Pohlmann is a Professor of Computer Science in the field of cybersecurity and is Head of the Institute for Internet Security - if(is) at the Westphalian University of Applied Sciences in Gelsenkirchen, Germany, as well as Chairman of the Board of the German IT Security Association TeleTrusT, and a member of the board at eco – Association of the Internet Industry.
References
[1] N. Pohlmann: “Ex schola pro vita – Studien- und Fortbildungsangebote zur Cybersicherheit”, KES – Die Zeitschrift für Informations-Sicherheit, DATAKONTEXT-Fachverlag, 3/2021
[2] TeleTrusT: “IT Security made in Germany”, https://www.teletrust.de/it-security-made-in-germany/





