Alternative Authentication Approach to Medical Devices
Markus Hertlein, XignSys, and Matteo Cagnazzo, if(is), explore solutions for securing and ensuring only authorized access to private health data.
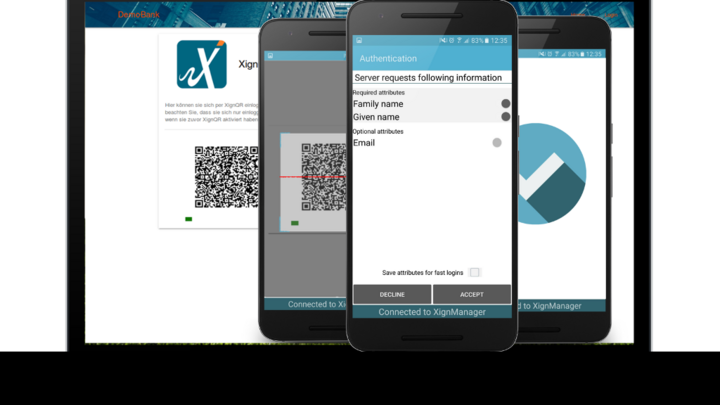
Image: XynSys

Markus Hertlein, CEO, XignSys

Matteo Cagnazzi, Researcher, if(is)
Listen to the audio interview with Markus Hertlein and Matteo Cagnazzo, or download it for later.
Modern medical components are often connected to the Internet or intranet, for example a hospital network, and therefore need authentication to offer services to an authenticating entity. The reasons why connectivity needs to be added are diverse, for example that the components are used for telemetry. The confidentiality, availability and integrity requirements for authentication and transmission mechanisms are also important. The mechanisms should be secure, easy to use and reasonably fast, so the user has no “waiting time” and the application becomes tactile and tangible. If we consider common contemporary mechanisms to authenticate against a service or a device, the most frequently used technique is username and password based approaches. These are prone to manifold attack vectors:
- Brute Force Attacks
- Dictionary Attacks
- Rainbow Table Attacks
- Key logging Attacks (Hardware and software based)
Since users tend to use unsafe passwords or the same password for multiple services, attacks on and over the Internet are becoming more and more profitable. But not only users tend to use unsafe passwords, vendors and manufacturers are also likely to use combinations like username: “admin” password: “admin” – as recent discoveries around the “Mirai” botnet show. [1]
One alternative is multi-factor authentication, which combines knowledge (username/password), ownership (smartphone) and/or individual biological properties (biometry). Access to a system is therefore granted if and only if the combination of all these challenges returns successful. A downfall is that a stolen "root-secret" corrupts a whole system and therefore most problems of password-based authentication are persistent and leading to a lower security level.
Generally, identities have different trust levels. Depending on the source which is used to verify one’s identity, a level of trust can be determined [2]
- Level 1: Data is not verifiable
- Level 2: Verification via Mail
- Level 3: Verification via presence
- Level 4: Verification via official document
Official documents are, for example, identity cards. These are a primary identity, and offer the highest level of trust. From those, secondary and tertiary-identities are derivable. One way to depict these different trust levels is via Public Key Infrastructure. The use of a PKI enhances also the security level of the authentication process. [3] Device and communication security in general is rather low in medical equipment. Drug infusion pumps can be remotely manipulated to change the dosage administered to patients and X-rays that can be accessed remotely by spying on a hospital’s network [4].
Hospitals are often unaware that these devices bring high risks to their infrastructure. Security flaws are publicly disclosed, but it does not change risk assessment in hospital environments. A common security vulnerability is the lack of authentication on such devices, but also weak or no encryption [5]. Former US vice president Dick Cheney had the wireless capability of his defibrillator disabled back in 2007 [6] – trust in networked medical devices is, as a result of such incidents, extremely low.
Proposed Architecture for connected medical devices
To be able to communicate with a medical device, one needs to authenticate against it. This can be done with a smartphone that scans a QR code attached to a smart object. The QR code only stores necessary information to identify the smart object on the server and a digital signature. After the QR code is scanned, the XignAPP validates the QR code’s signature and requests the information from the server of the smart object. All information is transmitted through the use of attribute certificates over a mutual authenticated secure channel. The benefits of the use of attributes certificates are that the information of the smart object can be verified regarding integrity and authenticity.
If the authentication is a non-critical component, like a smart radiator, the possession of the personalized smartphone suffices to fulfill the process. At critical authentication points, like defibrillators or insulin pumps, the smartphone will prompt the user to enter a PIN or use one or two biometrical authentication mechanisms. This process can also be carried out with a tablet or another mobile device. Instead of a QR code, another entry point can be used, for example a NFC tag or a geotag. After the scanning or initiation process, the process looks like the one depicted in Figure 1.
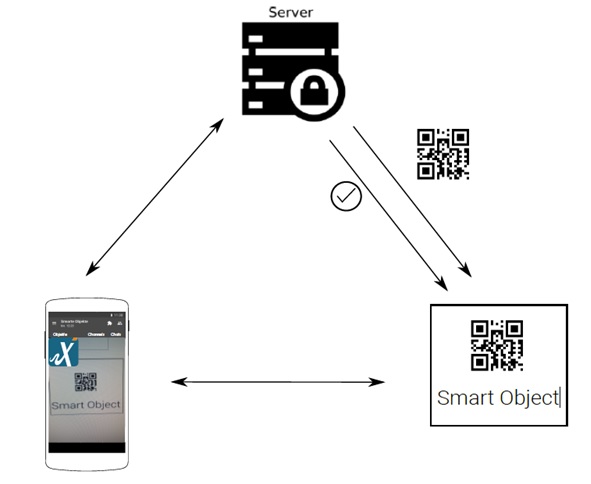
Figure 1: Schematic view of an authentication process
Every arrow in Figure 1 is a channel secured with TLS between the endpoints, and furthermore end-to-end encryption is deployed to verify and establish a trustworthy communication environment.
XignQR offers bi-directional communication channels through websockets, so the smart objects do not have to poll the server. This saves resources in terms of energy, which is an essential feature for resource-constrained devices. After a successful authentication process, all necessary information is transmitted to the smart object. This can be done on a high level with PKI-based attribute certificates or on a low level with a small uni-directional protocol.
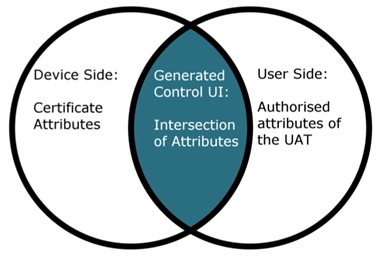
On the app-side, the smart object is shown in the user interface Quvert after a successful authentication and the user can control it from a mobile device or workstation. Quvert generates the available and necessary controls for the user only. The decision of how and which controls are generated is determined through the output of the attributes provided by the smart object and the authorization result from XignQR, the identity provider (Fig. 2). Most objects with a low trust level will be easily accessible with the smartphone, while more complex objects, for example medical imaging devices, will be visualized on a desktop application. The approach shown is not just limited to medical settings, but can be also used to realize a secure smart office [7] or to substitute passwords in classical authentication scenarios like user authentication on websites.
For further information on the approach and how to work together, feel free to contact either one of the authors.
Bibliography
https://www.symantec.com/connect/blogs/mirai-what-you-need-know-about-botnet-behind-recent-major-ddos-attacks [access 2016-12-09]
M. Hertlein, P. Manaras, N. Pohlmann: “Bring Your Own Device For Authentication (BYOD4A) – The Xign–System“. In Proceedings of the ISSE 2015 – Securing Electronic Business Processes – Highlights of the Information Security Solutions Europe 2015 Conference, Eds.: N. Pohlmann, H. Reimer, W. Schneider; Springer Vieweg Verlag, Wiesbaden 2015: https://www.xignsys.com/wp-content/uploads/ISSE2015-Paper-Bring_Your_Own_Device_For_Authentication-BYOD4A.pdf
Technology Nexus AB: Mobile PKI Security, Potential, Challenges and Prospects . In: https://www.nexusgroup.com/contentassets/0b5f8d23e4be466bb698b6f91769bb8f/nexus-white-paper-mobile-pki-en.pdf
A. Grau, 2015, http://spectrum.ieee.org/view-from-the-valley/biomedical/devices/hackers-invade-hospital-networks-through-insecure-medical-equipment [access 2016-12-09]
National Center of Biotechnology USA, 2015, Cybersecurity vulnerabilities in medical devices: a complex environment and multifaceted problem, https://www.ncbi.nlm.nih.gov/pmc/articles/PMC4516335/ [access 2016-12-09]
G. Kolata, 2013, http://www.nytimes.com/2013/10/29/science/of-fact-fiction-and-defibrillators.html?_r=0 [access 2016-12-09]
An Usable Application for Authentication, Communication and Access Management in the Internet of Things, Cagnazzo, Matteo and Hertlein, Markus, Pohlmann, Norbert, Information and Software Technologies: 22nd International Conference, ICIST 2016, Druskininkai, Lithuania, October 13-15, 2016, Proceedings, Springer International Publishing, p. 722-731
Please note: The opinions expressed in Industry Insights published by dotmagazine are the author's own and do not reflect the view of the publisher, eco – Association of the Internet Industry.



