Hospitals in the Focus of Cyber Criminals
Personal health information (PHI) is increasingly a target for cyber criminals - Hans-Peter Bauer from Intel Security explains why

Image: Intel Security
In recent years, E-Health has grown significantly. As in other industries, the healthcare sector is working towards maximizing efficiencies, containing expenses, capturing revenues, and delivering enhanced services through networked devices. While this brings obvious benefits, this move to digital healthcare also creates a great deal of personal health information (PHI), which contains protected health information such as family names, mothers’ maiden names, social security numbers, payment card and insurance data, and patient addresses. This also includes more sensitive information such as medical histories, details of medical conditions, mental health issues, medications, and treatments. If a patient’s PHI is up-to-date, it can help to increase the quality of patient care. For example, if a person has an accident, it is very useful for the ER to know if the patient is allergic to something.
An opportunity for cyber criminals
It is not surprising that the cyber crime community is starting to recognize that a person’s PHI has great value, which is resulting in these hackers targeting the medical sector. Intel Security has found evidence that data theft efforts go beyond financial account data, increasingly including medical records. The Intel Security Health Warning Report found that huge caches of detailed medical records can be purchased for a mere $0.03 to $2.42 per record.
We’ve found that cyber criminals already mine and analyze millions of such records, cross-reference them with data from other sources, and assemble profiles around individuals who appear to be the most viable targets for crimes such as blackmail. If personal medical data goes public, it can significantly impact someone’s life. With these details likely to be embarrassing or extremely sensitive for the patient, they are often willing to pay a great deal of money to ensure the data is not published. Unlike financial data, such as card numbers, once medical or personal information is released to the public, it cannot be changed or replaced.
As well as having a potentially detrimental impact on patients, medical hacks cause people to lose trust in their care givers. In this Second Economy, lost trust can inflict as much damage upon individuals and organizations as lost funds.
Why are cyber criminals targeting hospitals?
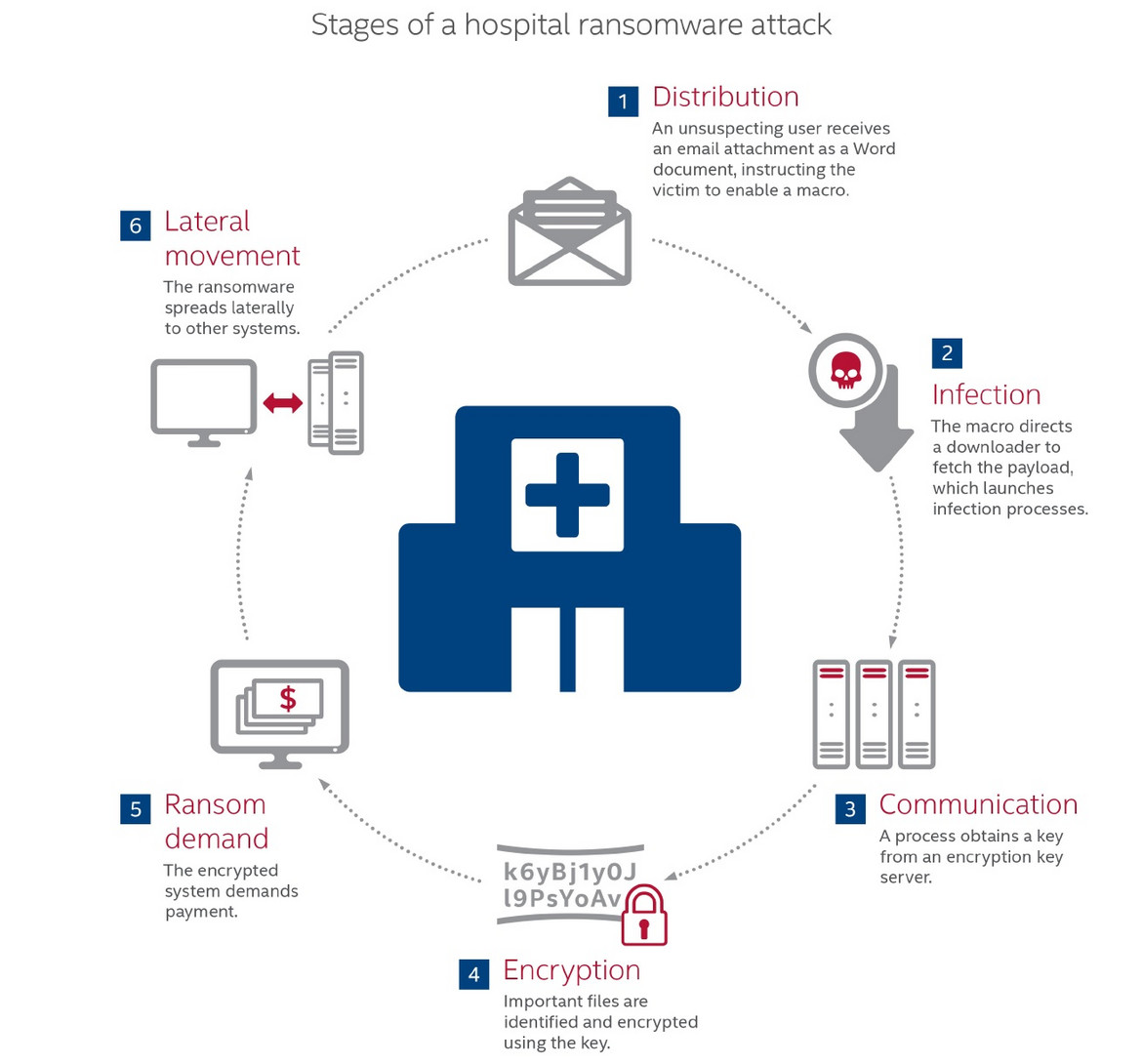
Hospitals are easy targets for cyber criminals. They have obsolete IT systems, medical devices with weak or no protection at all, third-party services and a wide range of data from a large number of patients. However, it’s not all bleak. Hospitals can undertake several actions to improve their protection. For example, they can perform business continuity and disaster recovery drills with the hospital emergency management team. By performing this during an incident and using endpoint protection and its advanced features, they can build a strategy to enable quick detection of threats. If possible, hospitals should also avoid storing sensitive data and ensure backup systems, storage, and tapes are in a location that is not generally accessible by systems in production networks. Most importantly, hospitals need to brief their personnel more efficiently, because most ransomware campaigns start with a phishing email that contains a link or a certain type of attachment.
It’s not just hospitals that are affected
Intel Security’s report also reflects on biotechnological and pharmaceutical firms being targeted. The criminals aim for intellectual property, such as formulas for next-generation drugs, drug trial results, and other confidential business information with significant value. The researchers have seen that the economic value of such information is considerably higher than the cost-per-record data that was identified within patients’ health care accounts. For example, the American Food and Drug Admission was targeted several times, because it is often the starting point for developing new products. Over 1,000 incidents were reported between 2013 and 2015. The range of attacks ranges from illegitimate, unauthorized access into the FDA computers to phishing and malware intrusions.
Cybercrime-as-a-service has become a normality in the cybercrime community, which is further helping the spread of such attacks. You do not need to be a proficient hacker to launch an attack, because cyber criminals support each other (for a price). Intel Security has identified cyber gang services available for hire specifically for the purpose of attacking health care organizations. Researchers found evidence of the purchase and rental of exploits and exploit kits to enable the system compromises behind health care data breaches.
In one case, a relatively non–technically proficient cyber thief purchased tools to exploit a vulnerable healthcare organization, and even leveraged free technical support to orchestrate the attack. The research found that this actor extracted more than 1,000 medical records that the technical support provider said was worth as much as $15,564.
In healthcare, gaining the upper hand in cyber security means rejecting conventional defense paradigms in favor of radical new thinking. Where they have undervalued cyber defense overall, they must prioritize it. Where healthcare organizations have relied on old playbooks, they must become unpredictable. Where they have hoarded information on attacks, exploits, and threats, the industry must become more collaborative. Not every security provider can be an expert in every area. Security experts need to work together to be able to provide a security architecture which enables good protection to the industry overall. Only by working together can we defeat cyber criminals.
Please note: The opinions expressed in Industry Insights published by dotmagazine are the author’s own and do not reflect the view of the publisher, eco – Association of the Internet Industry.



