The Cyber Resilience Act and its Impact on Security in the IoT
The EU’s Cyber Resilience Act will strengthen cybersecurity rules for hardware and software products. Tatjana Hein, eco Association, looks at what IoT manufacturers can expect.

©Natali_Mis | istockphoto.com
The Internet of Things (IoT) and IoT industry players together form one of the fastest and most sustainable growing industries in recent years. More and more objects are connected to the Internet and to other factors. Every second household in Germany, for example, already uses more than four devices with Internet access.
However, data security and the protection of user data often fall by the wayside. This ever-increasing networking of physical and virtual objects is prompting European Union legislators to try to regulate the sector.
The proposed Cyber Resilience Act (CRA) is particularly relevant for the Internet of Things. The draft, published on 15 September 2022, was already discussed in the Council in December 2022. The European Commission reached a political agreement on it in December 2023, which the European Parliament has already accepted and the Council is expected to adopt at the end of May. The Regulation is expected to enter into force later in 2024.
The CRA primarily affects software and hardware products with remote data processing solutions, specifically “products with digital elements.”
The aim of the CRA is to ensure that products with digital elements placed on the EU market have fewer vulnerabilities, that manufacturers are responsible for the cybersecurity of their products throughout their lifecycle, that there is greater transparency regarding the security of hardware and software products, and that users benefit from increased security.
The CRA is therefore both an opportunity and a challenge for the industry. This was the focus of a recent webinar hosted by the eco Association’s IoT and Security Competence Groups.
The current security situation in the IoT
Eric Clausing, Head of IoT at AV-TEST, gave an overview of the current security situation by reviewing certifications of IoT devices as well as unsolicited and private tests. This included the following categories:
- Local communication (e.g. Bluetooth, local network communication)
- Online communication (e.g. communication of the device itself or what is communicated on the server side)
- Mobile applications (e.g. investigation of potential gateways)
- Data protection and privacy (e.g. inconsistencies between privacy policy and actual data collection)
AV-TEST’s data on the security situation is based on honeypot systems that look like vulnerable IoT systems. More than 70 million attacks on these systems were registered and analyzed in 2023. Looking at the available figures for the first four weeks of 2024, the situation has not eased, with around 8 million attacks recorded in this period. What this means is that “if you put a device on the Internet, it is exposed to attacks within seconds”, says Clausing. A device with known vulnerabilities or corresponding vulnerabilities can therefore be considered to be infected within a few minutes.
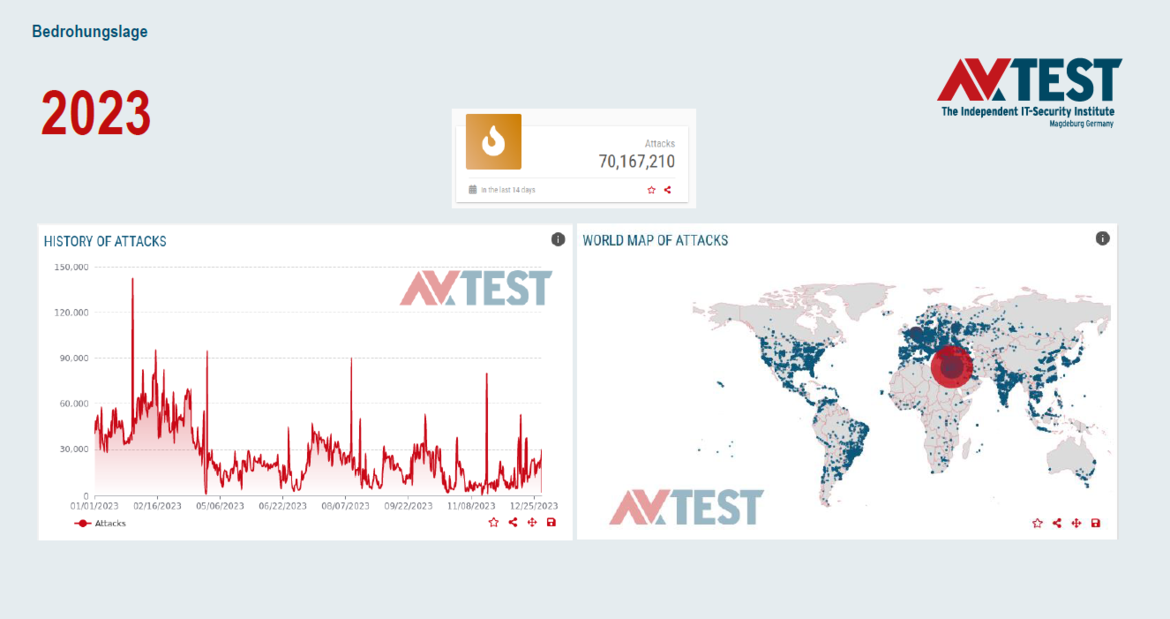
Botnets are still the biggest threat, with Mirai still in the top three. These are not highly complex attacks on devices but often target devices or entire device categories with weak or default passwords that are searched for and attacked. Often, these passwords are not changed by the users, or there is a lack of awareness about the importance of doing so, making such devices a very easy target.
Obligations as a step towards more IoT security
With more obligations on the part of manufacturers to secure IoT devices, such gateways could easily be prevented. Basically, it can be said that no device and no product category is exempt from attacks, so it is all the more important that IoT devices are equipped with a certain level of basic security.
What will the Cyber Resilience Act change?
Until now, there was uncertainty on how hardware manufacturers, including those from other European countries, would be subject to regulation on security of their devices and how retailers and importers were to be included in this scheme. The Cyber Resilience Act aims to resolve this.
The CRA is preceded by two relevant laws at the European level. Firstly, the NIS2 Directive from 2022 defines the IT security requirements for various IT services and products and creates a corresponding system for this. Secondly, the Cybersecurity Act of 2019 began to focus on the labeling of IT security for IT products. At the same time, however, the responsibility gap for smart devices (especially white-label products) was already being discussed and no one could be held liable in the event of vulnerabilities. These considerations then led to the Cyber Resilience Act, which is currently awaiting approval.
What does the CRA regulate?
The CRA aims to provide clear rules for the manufacturers, retailers, and importers of connected devices and their corresponding area of responsibility, and thus also to establish a labeling and compliance system. The CRA creates a three-tier system that covers various connected products:
- Normal Products
- Important Products
- Critical Products
However, the distinction here is not as simple as it seems, as Smart Home devices, for example, already fall under the “Important Products” category. “Critical Products” almost exclusively include products such as smart cards and the like, while “Normal Products” include products that somehow have an online function.
At present, it is not yet clear to what extent the Cyber Resilience Act will be accompanied by national legislation and how exactly it will be structured. This will presumably be defined in the CRA transposition acts at the national level.
The declared aim of the CRA is to ensure that products that do not meet these requirements are withdrawn from the European market.
Mandatory product cybersecurity – what can manufacturers expect?
Manufacturers have the most extensive obligations. This applies to both IoT devices and software products. Even if the CRA has not yet been passed and the national application laws are still pending, it should not be forgotten that product developments take at least two years, and therefore, the CRA requirements must already be incorporated into ongoing developments. “It is already high time for manufacturers to deal with the Cyber Resilience Act,” says Jan Wendenburg, CEO of ONEKEY GmbH.
The CRA will impose the following obligations on manufacturers of IoT devices:
- Create a security concept
- Carry out a risk assessment
- Use labeling to mark and identify their products
- Obligation to close or arrange for the closure of (manufacturer-) known vulnerabilities
- Mandatory naming of contact persons on site for administration and safety incidents in the company
- Obligation to update products for at least 10 years or the entire life cycle of a product
- Obligation to report active vulnerabilities
CRA affects manufacturers worldwide
Products not meeting these requirements may no longer be sold within the EU and must be taken back. In addition, manufacturers who fail to comply with the CRA risk penalties of up to 2.5% of their global gross turnover. This affects all manufacturers worldwide who want to sell their products in Europe, so it is “a de facto global regulation”, says Wendenburg.
SBOM – on the way to the CRA
As soon as the Cyber Resilience Act comes into force, manufacturers will be required to maintain a Software Bill of Materials (SBOM).
This is a systematic and structured record that describes the components of a software product and their relationships within the software supply chain. Manufacturers do not have to publish this record but are obliged to hand it over to the market surveillance authority upon its justified request. It is advisable to start creating SBOMs now to prepare for the requirements of the CRA. According to Thomas Seider of the German Federal Office for Information Security (BSI), it also makes sense for manufacturers of smart devices to be certified now in accordance with the BSI’s IT security label. This is a first step towards the Cyber Resilience Act, as some of the requirements are part of the IT security label.
SBOM – what is required?
The CRA clearly requires manufacturers to maintain a software bill of materials (SBOM) in a common machine-readable format, which at least shows the top-level dependencies of the product. The top-level dependencies of a product only describe the minimum requirements and are not particularly useful for cybersecurity. The manufacturer should therefore provide a more detailed list.
In preparation for the CRA, the BSI has published a technical guideline, TR-03183-2, in order to take an important step towards fulfilling the SBOM requirement before the CRA comes into force. The guideline is a recommendation on what an SBOM should ideally look like and how it should be set up.
More IoT security through legal obligations
The Cyber Resilience Act creates a regulatory framework with many obligations that are intended to strengthen and increase the cybersecurity of IoT devices in Europe. Many eco members have also long been calling for more obligations in the area of IT security for smart devices. This is the only way to introduce higher standards for cybersecurity in the IoT world and establish them in the long term.
The experts in the eco webinar emphasized that, despite many new requirements for manufacturers, which certainly also pose new challenges, the CRA must be seen as an opportunity for the Internet of Things and Europe. On the one hand, the CRA can be a competitive advantage for European manufacturers and, on the other, it will take cybersecurity in Europe to a whole new level. With the CRA, Europe can take on a pioneering role here, which can also ensure significantly higher security standards in the IoT globally in the long term.
With the implementation of the CRA, security aspects must already be taken into account in the development process of IoT products. If concepts such as security by design are implemented consistently, manufacturers will also benefit from lower costs in the medium term in order to meet the requirements of the CRA. The introduction of mandatory updates helps make products more sustainable, saving resources and reducing costs in the long term.
An additional effect of secure IoT devices through the CRA is the increased security of connected Internet and infrastructure. The CRA represents an important milestone towards greater security in the IoT and is welcomed by the industry.
Tatjana Hein is Project Manager IoT and Mobility at eco – Association of the Internet Industry. She is responsible for topics related to Internet of Things like smart factory, smart city, smart home, and for the subject area of mobility. Before joining eco in 2020, she was content manager and creator at a European analytics provider and was also a guest author for several magazines (such as Big Data Insider, Website Boosting, UPLOAD magazine, marconomy, Contentbird). Before that, she worked in an agency as a public relations manager for several start-ups.






