From Discovery to Defense: Mastering API Security in Modern Digital Ecosystems
Lisa Fröhlich, Corporate Communications at Link11, dives into the critical importance of API security, outlines common threats, and shares actionable best practices to protect sensitive data and ensure business continuity.

©putilich | istockphoto.com
Application Programming Interfaces (APIs) have become the backbone of modern digital systems, enabling seamless integration and communication between software components. However, this has created security challenges. The Salt Labs State of API Security Report 2024 reveals that 95% of IT professionals have experienced problems with production APIs, with 23% reporting breaches related to security flaws. The exponential growth of APIs has led to this issue, particularly shadow APIs that expand the attack surface and expose organizations to significant risk.
Shadow APIs evade detection, providing easy entry for attackers. A comprehensive API security strategy is essential to gain visibility into an organization’s API ecosystem. Studies show that 90% of organizations host shadow APIs, underscoring the need for increased visibility. By identifying and securing these hidden interfaces, organizations can protect sensitive data from evolving threats. Proactive measures that integrate API discovery, protection, and governance are essential to defend against modern attack vectors and ensure business continuity.
What is an API?
An API defines the protocols and rules for communication between software components. It allows different software programs to interact, regardless of location or platform. APIs can be divided into three main types based on their accessibility:
- Private APIs: Designed for internal use within an organization, these APIs are not public-facing.
- Semi-public APIs: Accessible in a public context but restricted to trusted entities to protect internal details.
- Public APIs: Available to external entities, enabling integration and communication with various applications and services.
While API security is most critical for public APIs, it should not be overlooked for private and semi-public APIs.
API Architecture

©Link11
The importance of API security
API security is critical because of the important role APIs play in connecting services and transmitting data. Breaches or vulnerabilities can lead to the exposure of sensitive information, including medical, financial, or personal data. The consequences of such exposure can be severe, resulting in financial loss, reputational damage, and legal ramifications.
Common threats to APIs
APIs today face a wide range of threats. Some of the most common include:
- DDoS attacks: Distributed denial of service attacks can render API endpoints unavailable or significantly degrade their performance.
- Data theft: APIs that provide valuable information can be targeted by competitors or data aggregators seeking to collect sensitive data.
- Account Takeovers (ATOs): APIs that facilitate user login are often targets for credential stuffing and other brute-force attacks designed to gain unauthorized access.
- Inventory denial attacks: APIs used for online shopping can be vulnerable to attacks that affect the availability of products.
API security vs. traditional web security
Securing APIs presents unique challenges compared to conventional web security. Traditional approaches often rely on a “castle and moat” strategy to protect a well-defined perimeter. In contrast, APIs have multiple entry points, creating a complex attack surface. Many APIs are accessed by mobile applications or services, which makes bot detection difficult. In addition, API requests can appear legitimate, making it difficult to identify malicious activity. The following table provides a brief overview:
Comparison of API Security vs. Traditional Web Security
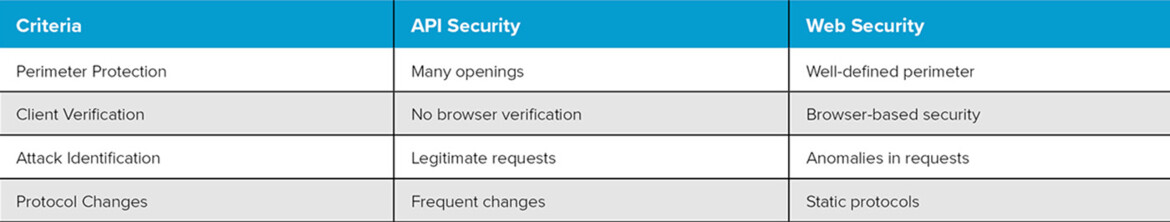
©Link11
API security challenges
API security is challenging. While APIs are subject to the same attacks as traditional web apps (e.g., SQL injection), many web app threat detection methods may not apply to APIs. Browser-based scanning cannot distinguish bots from humans because API traffic does not come from web browsers. The rise of microservices and serverless architectures makes it harder to secure APIs. DevOps often leads to quick API development without enough thought to security.
Best practices for ensuring API security
To mitigate API security risks, organizations should implement several key measures:
1. Authentication and authorization
Implement strong mechanisms for client identity verification and access control to API resources. It’s important to encrypt data in transit using secure protocols, such as HTTPS, to protect sensitive information from being intercepted.
2. Rate limiting
Enforce limits on client requests to prevent abuse and mitigate DDoS attacks. Rate limiting ensures API availability.
3. Input validation
Validate input to prevent security issues like injection and cross-site scripting (XSS). Rigorous input validation is key to maintaining API integrity.
4. Security auditing and monitoring
Assess the security of APIs through audits and monitoring to identify and address potential system weaknesses.
5. API traffic filtering
Leverage web security solutions designed to meet unique API security requirements. Effective filtering can provide protection from hostile traffic and mitigate potential attacks.
Best practices for enhancing API security
To effectively secure APIs, organizations should adopt several best practices. First, it is essential to restrict access from compromised devices, as rooted or jailbroken devices present significant security risks. Implementing strong authentication measures, such as multi-factor authentication, further helps reduce the likelihood of unauthorized access.
Additionally, employing obfuscation techniques can deter attempts at reverse engineering by making client-side code difficult to interpret. It is also crucial to avoid storing sensitive data on client devices; if necessary, strong encryption and secure authentication protocols should be utilized to protect this information.
Utilizing parameterized queries plays a vital role in preventing injection attacks by treating user input as data rather than executable code. Enforcing rate limiting is another important measure to mitigate abuse from high traffic volumes that may indicate malicious activity.
Finally, implementing comprehensive security solutions, including Web Application Firewalls, DDoS protection, and continuous monitoring, is essential to defend against various threats. By integrating these strategies, organizations can significantly enhance their API security posture.
Banking API security use case
Consider a banking application that relies on a mobile API for transaction processing. Securing this API is critical to protecting sensitive user data. Strong authentication mechanisms, such as MFA, are essential to keep user accounts secure. Rate limiting makes ATO attempts much more costly and difficult for attackers. Detecting jailbroken client devices (and refusing to run an application on them) helps prevent reverse engineering attempts. Minimizing (and, of course, encrypting) client-side data protects it from potential compromise. Robust input validation, perhaps even with parameterization, prevents attackers from submitting malicious input. Continuous monitoring of usage patterns can help identify anomalies and detect attacks in their early stages. By implementing these measures, the banking application can maintain its integrity and protect sensitive financial information.
Conclusion
Protecting against API attacks is critical to maintaining the security of modern web apps. Organizations must implement robust security, including authentication, data encryption, and continuous monitoring. By taking a comprehensive approach to API security, organizations can secure their systems, protect sensitive information, and ensure a safe user experience.
Experienced communications expert Lisa Fröhlich joined the Link11 team in May 2022. In addition to traditional PR topics and content management, she is responsible for corporate communications as the company’s spokesperson. In late 2023, she launched Link11’s IT security podcast “Follow the White Rabbit”. She gained extensive experience in the field of cybersecurity as a consultant for scientific communication at the Technical University of Darmstadt. Prior to that, she worked for over a decade as a PR Manager and Press Officer in the financial sector.
Please note: The opinions expressed in Industry Insights published by dotmagazine are the author’s or interview partner’s own and do not necessarily reflect the view of the publisher, eco – Association of the Internet Industry.




