Where DORA and DMARC Meet: Enhancing Financial Sector Resilience through Email Security
Matia Boldrini from Dmarcian examines how DMARC complements the Digital Operational Resilience Act (DORA), enhancing email security to bolster digital acceleration and strengthen the financial sector's resilience.

©Aleksandra Zhilenkova | istockphoto.com
In this article, we describe how the Digital Operational Resilience Act (DORA) intersects with Domain-based Message Authentication, Reporting and Conformance (DMARC), the email authentication protocol, showing how DMARC can complement DORA’s objective of making the financial sector more digitally secure and resilient.
What is DORA?
DORA stands for Digital Operational Resilience Act. It’s a regulatory framework proposed by the European Union in 2022 that applies to organizations operating in the financial sector. The regulation is now in force and will fully apply from January 2025. Appropriate safeguards are required to handle and respond to ICT (Information and Communications Technology) disruption and threats.
Under DORA, involved organizations must follow rules for the protection, detection, containment, recovery, and repair capabilities against ICT-related incidents. DORA explicitly refers to ICT risk and sets rules on ICT risk-management, incident reporting, operational resilience testing, and ICT third-party risk monitoring.
This regulation recognizes that even when a financial institution holds enough capital to cover traditional risks (market fluctuations, credit issues, liquidity shortages), ICT problems can create vulnerabilities to the detriment of stability in the financial system. This means that sufficient financial reserves do not necessarily protect against disruptions due to ICT incidents and operational weaknesses.
DORA is divided into the following seven chapters:
- General provisions
- ICT risk management
- ICT-related incident management, classification and reporting
- Digital operational resilience testing
- Managing of ICT third-party risk
- Information-sharing arrangements
- Competent authorities
DORA and DMARC intersections
Although DMARC itself is not explicitly mentioned in DORA, it can help achieve the objectives in each chapter by ensuring a robust cybersecurity posture, including protecting email domains from phishing and spoofing attacks to enhance communication security and operational resilience, as foreseen by DORA.
The following table summarizes the DORA Chapters where DMARC can help achieve its objectives:

DORA Chapter 2: ICT Risk Management
This chapter details the necessity for robust ICT risk management, including identifying, protecting, detecting, responding to, and restoring ICT-related incidents. With DMARC, organizations can identify email activities that are not duly authorized, reducing the risks associated with email fraud and helping an organization improve its reputation.
ICT risk management frameworks must include strategies, policies, and solutions incorporating information and ICT resources about threats like unauthorized access or use. Financial institutions are expected to reduce the impact of ICT risk by applying relevant policies and measures and promptly disclosing the relevant ICT risk to regulatory authorities. - DORA Chapter 2, Article 6
DORA Chapter 3: Incident Management, Classification, and Reporting of ICT
This chapter covers incident management, classification, and reporting of ICT incidents. DMARC helps detect and minimize the impact of security incidents resulting from email spoofing and phishing attacks, which pose typical threats to operational resilience and compliance.
Let’s not forget that one of the most prevalent, widely utilized attack vectors is phishing. Cybercriminals often leverage it to leak confidential data by convincing people to expose their personal information, login credentials, or financial details. For instance, most ransomware attacks start with an email-based phishing campaign where users are tricked into opening an infected file attachment or clicking on a malicious link.
Financial entities shall record all ICT-related incidents and significant cyber threats. Financial entities shall establish appropriate procedures and processes to ensure a consistent and integrated monitoring, handling and follow-up of ICT-related incidents, to ensure that root causes are identified, documented and addressed in order to prevent the occurrence of such incidents. - DORA Chapter 3, Article 17
DORA Chapter 4: Digital Operational Resilience Testing
This chapter deals with the digital operational resilience testing framework. A DMARC policy can be implemented and tested to prove its effectiveness in detecting and responding to email-originated threats, helping in a comprehensive cybersecurity strategy for any financial entity.
DORA Chapter 5: Managing Third-Party ICT Risk
This chapter deals with managing third-party provider risks. Including strong DMARC policies in third-party contracts is a significant step in maintaining the integrity and security of communication and, therefore, protection from email-based threats.
DORA Chapter 6: Information Exchange Agreements
This chapter focuses on the importance of sharing cyber threat intelligence between organizations and public entities for improving collective defense and response to cyber threats. Implementing DMARC across all domains can help identify threats like phishing and spoofing in email ecosystems.
A DMARC analytical tool, such as Dmarcian’s, is a core asset that enables the continued monitoring of any organization’s email ecosystem. It helps identify potential threats that could be shared in this intelligence effort.
Case Study: Banking Federation of Ireland members
The Banking Federation of Ireland (BFI) is the voice of banking and payments in Ireland. Its members include several financial institutions. We examined the implementation of DMARC among BFI members to provide insightful data on their email security practices.
Following are charts showing the DMARC implementation and policies for BFI members:
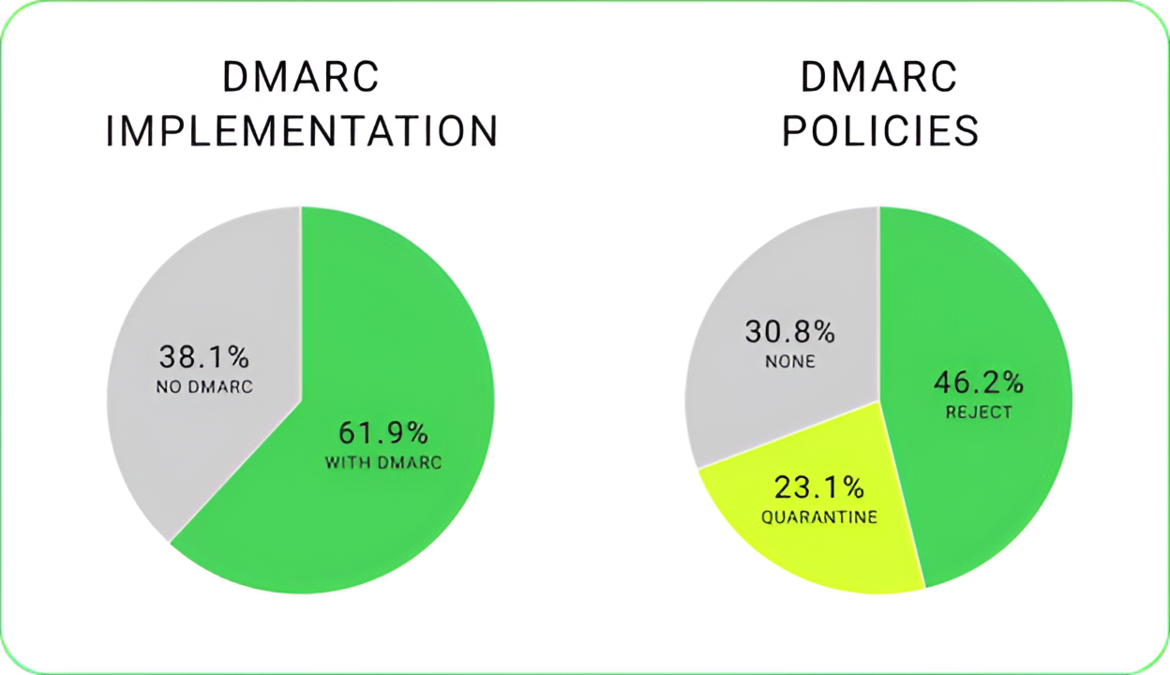
These numbers show that while 62% of the members have implemented DMARC to some extent, a significant subset (38%) still lacks the controls that DMARC can provide.
The data shows that 69% of organizations with an existing DMARC record have implemented quarantine or reject enforcement policies. However, there is still a need for improvement, especially for domains with a p=none policy (31%), which means having no protection against fraudulent emails.
DMARC is one of the building blocks in achieving DORA’s objectives of ensuring a secure and resilient digital finance sector. Financial institutions can benefit from deploying DMARC in their email systems, including protection from email-based threats, compliance with regulatory requirements, and upgrading operational resilience within their regime.
Financial entities should be planning the steps they will need to take between now and January 2025 to ensure that they can comply with this regulation and support the intended benefits of increased harmonization of digital operational resilience across the European financial system.
With 25 years of experience in the field of Information Technology, Matia Boldrini is a dedicated professional specializing in Messaging Security. Having previously worked as a Salesforce Developer, Matia is now the lead DMARC deployment specialist in the Dmarcian EMEA team.
Please note: The opinions expressed in Industry Insights published by dotmagazine are the author’s or interview partner’s own and do not necessarily reflect the view of the publisher, eco – Association of the Internet Industry.





