Securing Intelligent Healthcare
Verizon’s Alexander Schlager looks at security threats for IoT solutions in healthcare, and what to do about them.
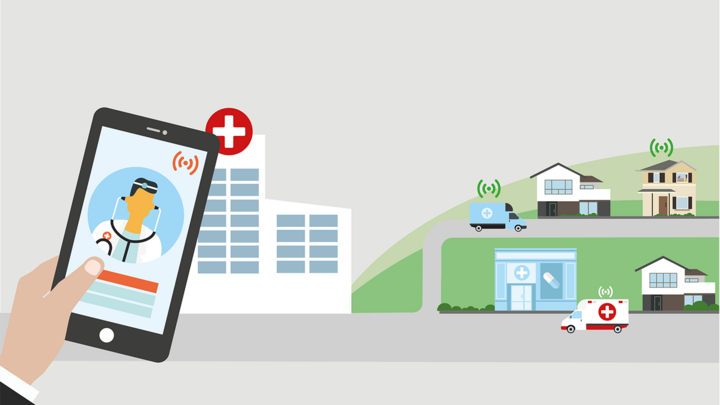
Image: Verizon
The world we live in is becoming more connected every day, moving well beyond emails and social media to a shared economy across many industries. For enterprises, the Internet of Things (IoT) presents huge opportunity to be more efficient, to find new ways to engage and keep customers and to transform the way business is conducted.
Within the healthcare sector, the use of IoT solutions can help hospitals better meet the demands of patients; enable better quality care and help in the tracking of inventory and resources. The potential impact could be incredible.
Consider, for example, the massive number of touch points in the pharmaceutical supply chain, from plant materials to packaged products on a store shelf. Today, companies widely use radio-frequency identification (RFID) technology to track the movement of products, but the technology is limited. It can tell when and where an item was scanned, but there is little to no visibility into what happened between two scanned points.
IoT solutions such as Verizon’s Intelligent Track & Trace provide a near real-time supply chain management platform enabling organizations to track, trace and monitor the condition of their drug shipments, particularly high value assets. Being able to track resources can also help reduce lost and stolen equipment, which could help organizations save thousands of Euros each year.
Another use case scenario is the use of IoT solutions to help patients on the go. Verizon is currently working with companies like AMC Health, a company that delivers mobile patient monitoring solutions via smart phones and tablets. Enabling patients to track their health via mobile devices, information that can then be accessed by their doctor so more timely and appropriate care can be taken when required.
Image: Verizon
However, what of the security threats for IoT solutions?
With IoT still in its infancy, it’s difficult to say with certainty what companies are facing. But we can look at what we do know. Of the projected five billion enterprise devices that will be around in 2020, not all of them will necessarily be Internet-visible, and not all devices will be sending sensitive data. In fact, many of them will be simple devices that have a single function — like a light sensor.
That said, any device that is connected, regardless of whether it’s IoT-enabled, is a potential target for a cyber attack. The devices themselves may not be the end target (they could be used to carry out malicious activity as part of a botnet attack), but they could be used as a gateway into the broader enterprise network and critical systems.
IoT is all about making the things around us smarter, but the use of many sensors, especially those embedded in assets, must be prudent. Limitations on space mean that processing power and battery life are often limited. This means that many sensors aren’t capable of running the endpoint protection capabilities we’re used to seeing in more sophisticated assets, like laptops.
Security considerations
As use of IoT solutions become more widespread within businesses ranging from healthcare, manufacturing to energy and utilities, they will become core business enablers, and as such, the security of these elements should become a core business initiative and form a fundamental part of a business’ comprehensive security strategy.
As a result of the complexity of IoT ecosystems, there are a number of aspects (or “layers”) all businesses should consider in relation to their security. These are as follows:
1. People – Creating a 'security aware’ culture amongst employees that instills awareness, responsibility and accountability is crucial. This should be underpinned by educational activities emphasising the importance of security within the business environment.
2. Physical – Just like with normal security best practise, physical security measures should be taken – from locks to surveilence systems – in order to protect the actual sensors located on a site. For example if these sensors are physically removed/stolen from their location then the data collected is less accurate.
3. Device/Hardware – Some best practises include:
- Device Hardening – turn off services that are not needed.
- Testing - Perform penetration tests on the hardware to discover vulnerabilities or other security issues.
- Passwords – Change the default password and use a strong password policy.
- Risk – Assess the risk based on what the IoT device does and take appropriate measures – for instance a medical device such as an insulin pump can potentially have a greater harmful impact than a sensor that just maps foot traffic in a retail store.
- Privacy – Collect only the data needed and encrypt this data when in rest, in use or in transport. This counts for all protection layers, not just the device layer.
- Component level – If security measures are available at this low level and if it is feasible, enable this as part of the layered defense.
4. Application – Best practices should be used for IoT applications. For example, the Open Web Application Security Project (OWASP) and Security Lifecycle Development. Regular testing should also be done to validate that these best practises are being followed and to discover any vulnerabilities or other security issues that may exist.
5. Network – Take appropriate measures to secure the transport layer and channel of the IoT devices so that the traffic cannot be intercepted, altered or disrupted. Also consider monitoring this traffic to see if there is an incident occurring.
Image: Verizon
Ensure the security basics are in place
Cyber criminals will target any business or industry, regardless of size – as long as there is data and goods that can be monetized. Many businesses that fall victim to cyber attacks don’t have basic security practices in place, such as identifying the assets and data most critical to an organization and placing stronger controls to manage the risk. Overlooking the most basic steps can lead to disaster.
The same familiar security rules also apply in this new IoT environment – remember to authenticate all IoT connections; ensure that patches are applied to IoT devices promptly; only collect the information that is required from IoT devices, and dispose of it securely when it is no longer needed; encrypt sensitive IoT data and segment IoT networks and systems to limit the spread and damage of any attack
As IoT devices become more widespread and more closely integrated with core systems, it becomes more important that security is made paramount from the start. Just as with any other IT system, organizations across all verticals should regularly assess the risk, apply appropriate security measures, and test their effectiveness.
Please note: The opinions expressed in Industry Insights published by dotmagazine are the author’s own and do not reflect the view of the publisher, eco – Association of the Internet Industry.



