Gaining More Insight into Malicious Domains
Theo Geurts from Realtime Register B.V. describes a proactive approach to malicious domains, based on analyzing and sharing data, and responding to incidents.

© ValeryBrozhinsky | istockphoto.com
Registrars have taken different approaches towards addressing malicious domains. Some remain more reactive, which means that their anti-abuse work is mostly focused on reviewing the reports of abuse that they receive. On the other hand, others have decided to be much more proactive and go beyond the mere receipt of the reports. One of the latter is Realtime Register, who have an Abuse Insight monitoring system that they put together over the course of several years.
An Effective Anti-Abuse Implementation
In 2017, Realtime Register introduced an approach focused on incident response rather than on the receipt of reports. This approach provided them with detailed information on how cybercriminals operate (which they didn’t have before, and which allows them to be much more effective in addressing abuse). However, it requires external tools and a process in which every abuse report that is received is strictly documented and analyzed.
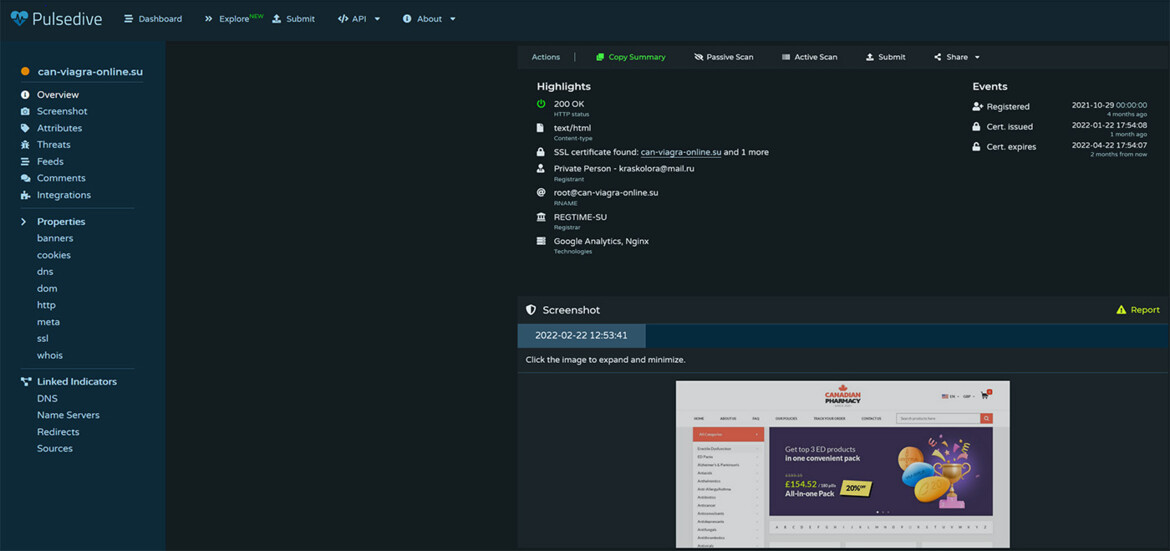
It’s a combination of good data sources, sound systems, and an effective process. It was all built around five principles: Gather, analyze, share, exchange, and respond, referring to what can be done with threat intelligence in general and, in particular, regarding malicious domains: Gather data from high quality domain reputation feeds, use good analysis tools that allow detailed correlations (visualizations are a great plus), share with registries, resellers and other parties who can act on the information to mitigate the threats, exchange information with those who may have related information that is of interest and respond by acting on the actionable information in order to mitigate the threats.
Reseller Access to a Visual Dashboard
Realtime Register currently use Microsoft’s Power BI, which provides visualizations, has some nice analysis features, and is also a platform to create dashboards. And the dashboard is available not only to Realtime Register: Very importantly, they make it freely available to their resellers. It was the cheapest option for their existing settings, making it the easiest solution for then to get started with.
In the dashboard, resellers can:
- See data like abuse percentages for their domain portfolio calculated based on PulseDive.com abuse data, rescan domains, and see the source of malicious activity. Each reseller can see the ratios per abuse type within their portfolio, so they know that they have X% of malware domains, Y% of phishing domains, and so on.
- Resellers can zoom in on one given indicator or domain and see more details. Also, they can see the source reputation feed that lists the domain and the kind of activity that it was listed under.
- When zooming in on a particular domain, they can see the subdomains and URLs associated with it, which provide even more information about the abuse.
- Resellers can then zoom in once again, this time on the particular feed itself that provided the listing, where they will find all the specific details of the abuse with the corresponding analysis and all other available data.
- The data from Pulsedive goes back to 2018 and provides historical context to the resellers.
- Zoom in on other reputation blocklists available (75+)
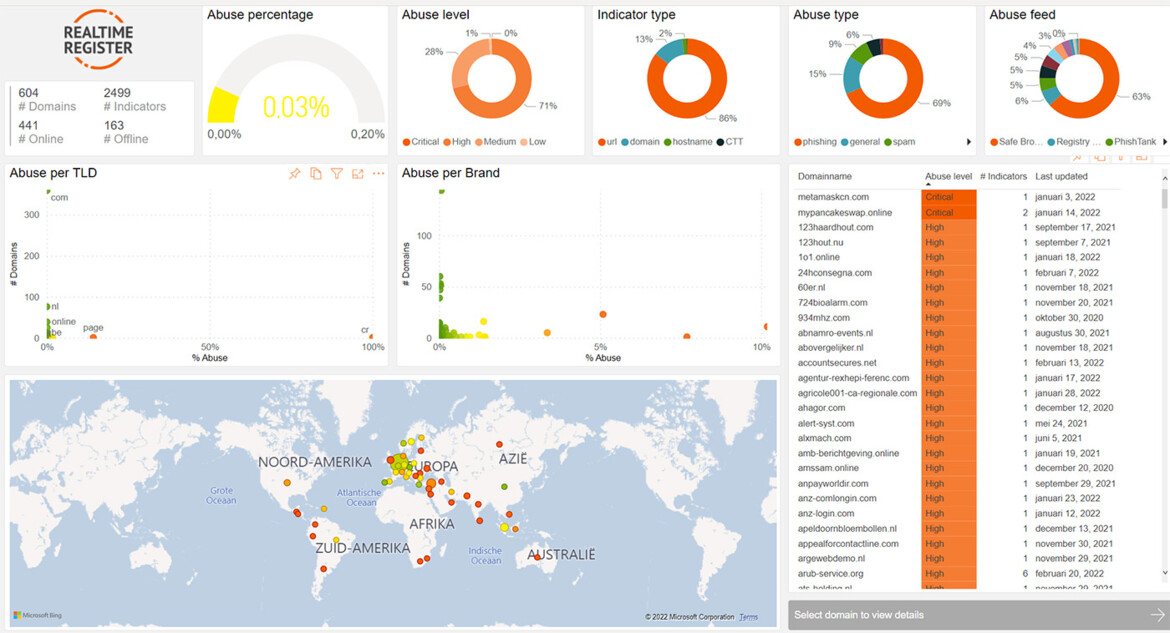
The dashboard is updated every 24 hours. For all feeds (except some that are updated every hour), Realtime Register additionally sends a notification of abuse report events through an API or via email to the corresponding resellers (often hosting companies).
According to their analysis, since 2018, the average abuse percentage of DNS abuse at Realtime Register is 0.03%. They intend to continue using their systems and process to keep it well under control.
Predictive Analysis
To stay ahead of the game, a system has been set up that runs in the background and reviews each newly-registered domain name to check metadata, assign a scoring, and generate a daily report indicating which domains may become malicious and may warrant extra investigation. When a domain is included in this report, the next step is to check whether the registrant data is bogus or corresponds to an already-known malicious registrant and whether the domain is associated with other data points already known to be related to malicious activity (like IP addresses, name servers, and others)
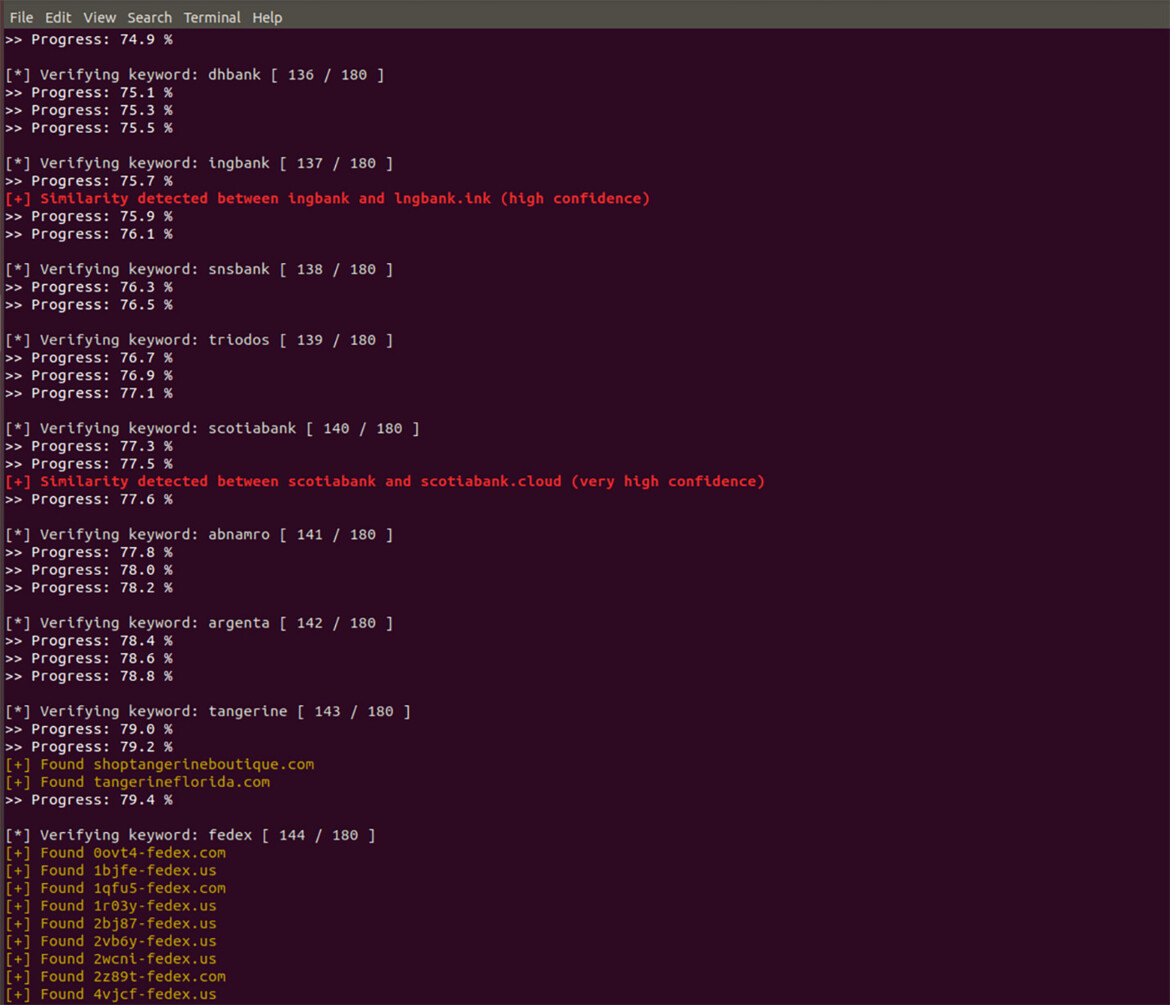
It still requires human review because there still are false positives, but it works. It lets us see what’s coming and stop it before it does any harm, like in banking phishing.
Conclusion: Commercial Benefit
DNS abuse raises costs for registrars who have to do all this anti-abuse work. Margins are thin, but abuse prevention results in lower costs, and resellers are in a position to claw back some of those costs. Certain registries also factor in abuse levels in calculating discounts and promotions for registrars, which are sought after because they provide better margins.
Also, by being proactive and suspending domains in advance of them being used, they ensure that they don't get reports of abuse, which are expensive to deal with.
In other words:
- Preventing the creation of malicious domains means reduced costs associated with the anti-abuse work required to deal with malicious domains.
- Properly addressing the malicious domains that do get created can result in discounts from the registries to the registrars, which could help their sales increase with even higher margins.
So, there is commercial sense in a registrar doing anti-abuse work. It is not just a dead cost, a burden. In the case of Realtime Register, they keep their good reputation, they probably are treated very well with discounts by the registries who also benefit from cleaner TLDs, their resellers stay clean, and the global Internet benefits from a cleaner domain name industry.
This is an example that other registrars could follow. Effective anti-abuse work that brings commercial benefits. Why not?
Theo Geurts has worked within the DNS industry for over a decade and contributed to many of ICANN's policies. For the last four years, Theo's focus has been on Cyber Security, OSINT, and ethical hacking. He played an essential role in DNS Abuse investigations ranging from BEC fraud to cyber terrorism.
Please note: The opinions expressed in Industry Insights published by dotmagazine are the author’s own and do not reflect the view of the publisher, eco – Association of the Internet Industry.




