The Debate around Defining, Preventing and Mitigating DNS Abuse
What is DNS abuse? Simone Catania from InterNetX looks at the definition of DNS abuse and describes scenarios for prevention and mitigation.

©MicrovOne | istockphoto.com
DNS abuse is becoming an increasingly thorny issue for registries and registrars worldwide and ultimately for the global Internet audience. Solving DNS abuse or mitigating its effects requires a joint effort and some centralized functions and coordinated activities among the stakeholders. Recently, awareness around the topic appears to be growing and recommendations have been put forward.
DNS abuse is an important issue for the Internet ecosystem, one that requires more attention and urgent action. In this article, we want to introduce the topic of DNS abuse, outline the current problems concerning its definition and describe preventative and mitigating scenarios.
The definition of DNS abuse requires globally recognized boundaries
One of the main problems in the DNS abuse debate originates from its very definition. As of today, a globally recognized definition of DNS abuse is lacking, as stated by ICANN, who also pointed out the urgency around this issue. Since there are no clear boundaries in DNS abuse, it is hard to define it accurately. A recent study on DNS abuse conducted by the European Commission has come up with this rather blurry definition:
"Domain Name System (DNS) abuse is any activity that makes use of domain names or the DNS protocol to carry out harmful or illegal activity".
So, what are these harmful or illegal activities that exploit the DNS? They include these five broad categories:
- Botnets
- Malware
- Pharming
- Phishing
- Spam (when used to spread other DNS security threats)
Compromised vs. maliciously registered domain names
To define DNS abuse, it is important to make a clear distinction when discussing "abused" domain names. What seems to be internationally recognized is the differentiation between maliciously registered domain names and compromised domain names, the latter being domain names registered legitimately but subsequently taken over by cybercriminals.
1. Domains registered with the deliberate intention to harm
This is the first question we should ask ourselves. Is the domain registered maliciously? To answer this question, you could visit the website and see if valuable and trustworthy content is available. Then, check the WHOIS database. If the domain was registered only a few days before it got blacklisted, then a red flag should be going up.
2. Domains of hacked websites used to harm
Domain names might have been registered legitimately. The website gets compromised to serve illegal content and phishing campaigns. The legitimate domain names are usually registered many years before and the domain name is valid. A small percentage of abuse is perpetrated at the DNS level, such as domain shadowing attacks. The most substantial number of domains are abused at the website level because of vulnerable software like the Content Management System (CMS).
How can you distinguish between compromised domain names and maliciously registered domain names? There are two main approaches.
1. Verification techniques carried out by humans
Individuals can verify a great deal of information related to the domain and draw conclusions. The age of the domain name and the time span between the registration and the blacklisting. Registrations carried out in bulk are also often a red flag. Techniques like cybersquatting, i.e., using a misspelled version of a brand name or service, are also relevant here.
2. Verification techniques carried out through machine learning
Nowadays, there are many approaches based on machine learning. These were developed by different parties in order to achieve high accuracy in classifying domains based on publicly available data.
Why is defining DNS abuse so complicated?
DNS abuse has different typologies and there is significant overlap between different types of abuse. It acts in a large ecosystem composed of multiple public and private players (domain resellers, registrars, registries and hosting providers) that operate on a national, regional and international level to maintain the technical infrastructure of the DNS.
Furthermore, there is an intrinsic difficulty in creating a clear division between technical security and content-related abuse. Too often, the boundary is neither clear nor straightforward. For example, phishing attacks involve both malicious domain registrations and malicious website content. A piece of malware might exploit DNS vulnerabilities and spread harmful content on a website. At what level should DNS be fought and prevented? Who is in charge? These are two of the most crucial questions in the DNS abuse mitigation debate that we will try to answer.
An overview of DNS abuse in 2022
At the end of January 2022, the European Commission published a report on DNS abuse. To assess the impact of DNS abuse, the authors conducted an overall health check of the top-level domain (TLD) ecosystems and different intermediaries such as domain registrars, hosting providers, and providers of free services. Concerning DNS abuse, the main findings from the report were:
- In relative terms, the most abused TLDs are new gTLDs.
- The two most abused new gTLDs account for 41% of all abused new gTLD domain names, which means that not all new gTLDs experience DNS abuse to the same extent.
- European ccTLDs are the least abused domain names in absolute terms.
- Most spam and botnet command-and-control domain names are maliciously registered. Legitimate users registered about 25% of phishing domain names and 41% of malware distribution domain names. They were compromised at the hosting level.
- The top five most abused registrars account for 48% of all maliciously registered domain names.
- The general adoption of DNSSEC remains low.
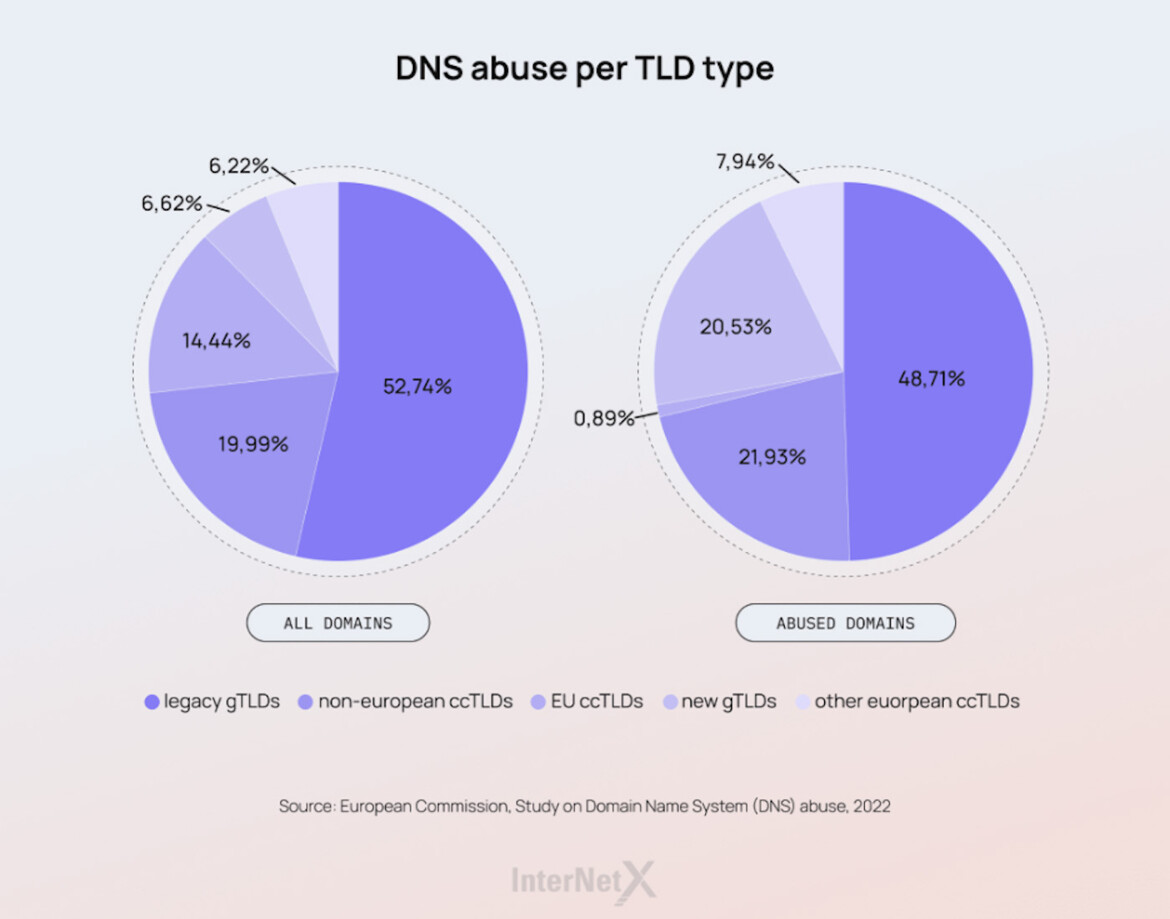
It is important to highlight that, for the first time, the EU has provided a helpful study that does not focus only on the “abused parties” but also on the intermediaries. The study proposes means of prevention, detection and mitigation of DNS abuse addressed to DNS operators as well as international, national, and EU institutions and coordination bodies. Although the report shows some misleading analysis and inconsistent conclusions (as reported by CENTR), it does provide a clear signal that DNS abuse is being taken seriously and we can expect further development on this issue in the near future.
Preventative or reactive DNS abuse mitigation?
Before implementing cost-driven measures and initiatives, the first thing you should do is identify a mitigation framework. The industry has implemented both reactive and preventative actions.
“Reactive initiatives” refers to all actions carried out by registries and registrars after receiving a report of abuse. It involves the investigation and mitigation of the threat once it has already been deployed. When undertaking reactive initiatives, your sphere of control only lies in improving the quality of the reports and the speed at which you react to warnings.
Developing reactive responses to mitigate DNS abuse is absolutely indispensable. Still, we believe that focusing on preventative methods and detecting potentially malicious domains before registration is completed, or before the domain resolves, is the right course of action. No matter how quickly you catch a threat in a website or domain name, it was there already and the extent to which it affected users is unknown. You can only hope that the damage was negligible. Preventative measures are cost-efficient in the medium to long term and they certainly have a significantly more positive impact on business. But above all, they protect registrants from possible threats, since they are caught at an earlier stage, i.e. the threat is stopped before it reaches anyone.
Where can you deploy preventative methods?
If you wish to carry out preventative measures to mitigate DNS abuse, one option is to analyze the domain name registration before the data is forwarded to the registry. Registries do not have much information about the registrant. Registrars are the intermediaries who collect most of the data.
For example, they have far more information about who is carrying out the transaction, e.g. credit card details. The payment process presents a good opportunity for mitigating threats. Nowadays, payment services providers offer fraud detection, and a suspicious payment authentication could be suspended altogether from registering a domain name. Other information revealed during the domain registration process, such as the registrant’s name, IP address, and the domain name itself, can prove helpful as well. For example, particular keywords in the domain names might trigger a red flag. A great working model of this is provided by EURid, registry of the .eu TLD. The registry developed an AI-based warning system against domain misuse that looks for patterns in domain registrations and delivers a prognosis on whether a domain may potentially be used in an abusive manner later on.
Why is DNS abuse mitigation challenging to implement?
The problem with preventative measures is that they often cause friction in the registration process. In recent years, registries and registrars have put a lot of effort into making domain registration easier. You need dedicated employees who write and integrate extensive and complicated code to carry out preventative measures. These actions bring no direct revenues to the players that make up the Internet ecosystem, which are primarily commercial entities. A real DNS abuse mitigation also needs to be sustainable for companies, or cost as close to nothing as possible.
Who should mitigate DNS abuse?
There are three possible scenarios for identifying who could mitigate DNS abuse.
Scenario 1: Generally, the action needs to be taken at the DNS level for domains. Therefore, we need to consider the players involved in the registration process. If available, we start from the domain reseller and work back to the registrar and TLD registry.
Scenario 2: There are two different scenarios for malicious content. You start at the hosting level with the hosting reseller and hosting provider and then look at the DNS level for maliciously registered domain names. But when the domain name has been compromised, such as phishing content, you could start operating directly with the hosting operator.
Scenario 3: If the abuse concerns DNS operations, such as DDoS attacks against a DNS server, the measure needs to be addressed at the nameserver level.
DNS abuse mitigation for a safer Internet
It should be clear now that the diverse Internet ecosystem makes it difficult to report abuse in any single meaningful way. Unfortunately, accomplishing the scope required has not been a core competency or primary goal for most organizations, including registrars and registries. Nevertheless, there have been more discussions around this issue from ICANN and other institutions recently.
There is certainly a long way to go before we are able to define clear paths forward, but we are confident that these are only first steps for much broader interest and global action.
Simone Catania currently serves InterNetX as Global Content and Communications Manager. He is responsible for the content across InternetX's blog and other channels and helps users understand the underpinning mechanisms behind the Internet. Simone is an ICANN fellow and member of EURALO and UASG.
Please note: The opinions expressed in Industry Insights published by dotmagazine are the author’s own and do not reflect the view of the publisher, eco – Association of the Internet Industry.





