Secure Home Office in Times of the Corona Crisis
With the right measures, you can provide for secure home office workplaces where company & customer data also remain protected, Markus Selinger from AV-Test explains

© NicoElNino | istockphoto.com
This article is published with the kind permission of AV-Test and was first published on their website at: https://www.av-test.org/en/news/secure-home-office-in-times-of-the-corona-crisis/
Working in home office during the difficult times of the coronavirus pandemic is a good alternative for companies to protect employees and the enterprise. Smaller companies and self-employed individuals, however, do not have the IT infrastructures of large corporations. With the right measures, you can provide for secure home office workplaces in which company and customer data will also remain protected.
In large corporations, IT managers normally utilize all available tools to ensure that employees can work securely in their home office. They typically have corporate notebooks for that purpose, with everything already on board to connect securely with the corporate network. If private notebooks or PCs are used, there are normally virtual machines (VMs) set up according to corporate policies. They allow no data exchange between PCs and VMs and thus ensure secure working. Endpoint security solutions often also monitor data traffic in the background and provide additional security modules.
Secure working in the home office
Smaller companies, startups, or self-employed individuals who manage customer accounts often do not have such sophisticated IT structures to fall back on. But the market offers several possibilities here for secure working from a remote location. With the following tips, you can create a secure IT work environment in the home office for you and your employees.
Tip 1: Remote access per remote control
If there are no remote access points or relevant servers, there are tools available for remote control. A well-known option here is the embedded Windows feature, Remote Desktop Protocol, or RDP for short. This solution, however – if it is to be secure – has to work with a matching server and requires additional security measures. A faster method involves secured service tools for remote control access. Widely available options include TeamViewer, LogMeIn or Radmin. The clients of the tools can be installed on corporate PCs and run continuously in the background. Via PC or notebook with the access software, the corporate PC can be used with an ID and a strong password as if the user was sitting in front of it. Additional use of two-factor authentication ought to be mandatory here
Advantage: The tools can be quickly installed, activated via license, and used by almost anyone, without requiring extensive prior knowledge. Work can continue as usual, as if the user was sitting at the PC.
Disadvantage: An administrator loses overall control over which user is dialing in. Any available corporate network may thus be open to the outside. This solution is only something for individual PCs and should not be used on a long-term basis. Strong passwords and two-factor authentication are also mandatory here.
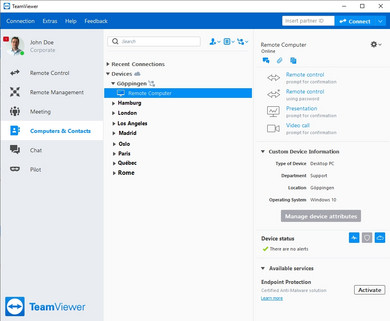
© Team Viewer
Remote Control with Team Viewer
For secure remote access, it is worthwhile using a good tool, such as the well-known TeamViewer, which is easy to operate.
Tip 2: Secure connection via VPN
For security purposes, even secured corporate notebooks connect to the company via Internet only per VPN (virtual private network). This secure data tunnel from an external PC or notebook into the network can practically not be hacked and also uses encryption. For private use or for smaller companies, instead of large client-server solutions, there are also service providers for smaller platforms with fewer licenses. Suppliers of remote control software also offer a VPN connection service for a supplemental fee.
Attractive for smaller companies: Some DSL routers can be coupled with a second device of the same brand and automatically work with one another only with encryption and secured per VPN.
Advantage: It is not possible to hack into the line, as the connection is practically point-to-point, and there are no detours via unsecured servers.
Disadvantage: Setting up the solution is technically sophisticated and normally associated with more costs.
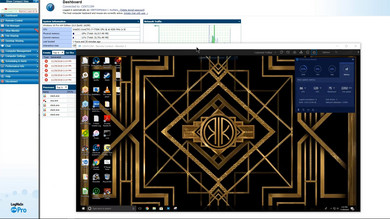
© LogMeIn
Remote Control with LogMeIn
The LogMeIn tool provides for secure remote access on corporate PCs and also features additional useful tools, such as password management, storage space, or remote printing.
Tip 3: Secure emergency platform for digital data rooms
In case a small company believes that connecting up per remote access or VPN would be too risky, it can fall back on so-called data rooms. Leading global suppliers here include Brainloop or IDeals. Depending on the country, there are also prominent local suppliers whose portfolios are tailored more to smaller companies. In principle, these are cloud storage servers where work data can be safely offloaded and edited. They also provide for implementation of an access structure for existing data and employees, in the same way as it is normally handled on a corporate server. There are many providers of these data rooms on the web. Some providers even offer this service to their customers.
Advantage: High security for data against outside access, despite outsourcing. As the data rooms are also certified for due diligence or M&A, the increased access protection is provided and allows no weak passwords. Moreover, data rooms can be quickly set up and are easy to administer.
Disadvantage: The data can indeed be sent and received per email or uploaded or downloaded out of the data room. Documents may also end up on the employee's private PC, however.
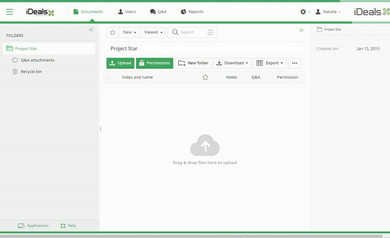
© iDeals
Secure Data Rooms as a Platform
If no data servers exist in the company, data rooms, including user administration, can also be used as team workplaces.
Tip 4: Videoconferences instead of personal meetings
Instead of meeting face-to-face, videoconferences have already offered an alternative for quite some time now. Especially in the home office, this type of conference can be quickly and easily managed. For small teams that cannot conference due to the coronavirus, the well-known Skype service is available. The client is usually preinstalled on many pieces of equipment, as well as on personal devices. But there are also many services that can be centrally managed and through which one can invite other employees per email. That's how it works with Amazon Chime (basic version free of charge), GoToMeeting, or WebEx from Cisco. Some remote-control packages also have a built-in videoconference tool. The tools mentioned above normally only allow for the exchange of data.
Advantage: The videoconference tools are easy to manage and also offer a secure connection. They allow for screen sharing and easy data exchange. Those who do not have a PC available can normally at least participate in the conversation by phone. Almost everyone has access to systems such as Skype. As an additional feature, they also allow for continuous chat.
Disadvantage: For videoconferences, there needs to be a certain level of conversation discipline, otherwise they will result in everyone's talking at once and in some kind of cacophony. Long videoconferences are often more strenuous than real conferences.
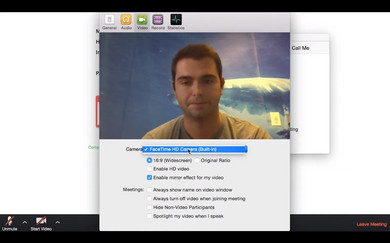
© Zoom
Videoconferences Instead of Meetings
Online conferences, such as here with Zoom, for example, can be quickly and easily organized on many devices, whether it be PCs, Macs, or mobile devices running on Android or iOS.
Tip 5: More security for external notebooks and PCs
If employees need to use their private IT structure, they ought to observe a few points to ensure a high level of security:
- The PC should always be equipped with good security software. The latest tests from AV-TEST indicate which products meet this criterion.
- Application programs on the PC ought to always be up-to-date. Users often have a software updater included in their security solution. Should that not be the case, this can be solved using a free tool, such as Patch My PC (for individual PCs). For several devices and systems, there is a free service from ManageEngine. But it is an online service that requires system access.
- For emails, you should not use your private account. It is better to access corporate emails via a web client. Access is secure even if the user's own PC is infected with malware.
- For more security, dialing into corporate servers or via remote software ought to always be handled per VPN software.
- If corporate data is to be edited, users should not temporarily store it on their PC but rather on an external hard drive or a cloud storage server. Both media are quickly available within the company at the end of the home office period or can be more easily passed on to colleagues in case the user should become ill, for example.
- Strong access passwords should be additionally protected by means of two-factor authentication, e.g. per text message code or other security tokens.
Increased danger due to phishing with "coronavirus" spam and malware
Cyber gangsters have no heightened sense of morals even at times of the coronavirus crisis. They exploit all users' need for information, send out an increased volume of spam and infected emails on the topic of "Corona", using these for phishing attacks.
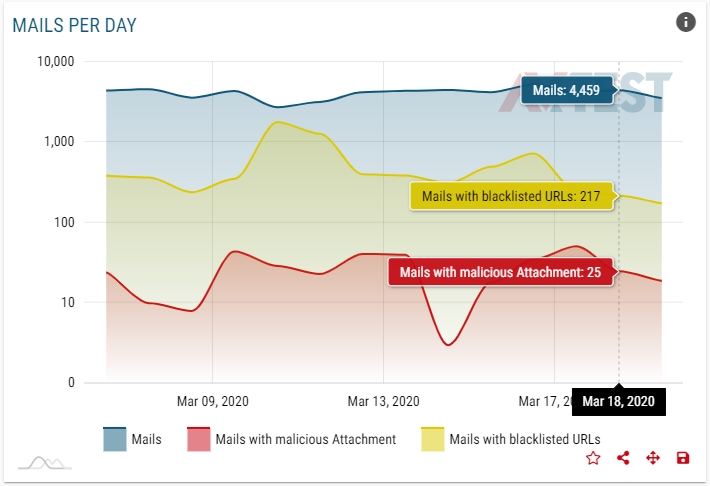
© AV Test
The new platform, AV-ATLAS, shows in real time the development of spam, the country from which it is currently being sent out the most, and which message texts are being used the most for spam mail. In the overview, you'll also find the latest malware trend, along with the analysis of suspicious Internet addresses. You can find out about all the features the AV-ATLAS has to offer in the article "AV-ATLAS: Real-Time Threat Analysis".
AV-ATLAS shows the current security situation. It is up to each company, with the help of this information, however, to provide for effective employee rules of conduct in terms of security. In case employees in the company have not undergone any security training, company owners should urgently see that they do so. This ensures that all employees will be sensitized to the current situation and the resulting heightened cyber danger. That is why you should observe the following points in particular:
- Check all emails with links and file attachments with increased suspicion. If anything appears strange, contact the sender by phone prior to opening links or file attachments.
- Especially watch out for emails with the topic of "Corona" from all senders – even from known addresses.
- Before you click on an insecure link, you can check this yourself in the email program: without clicking on it, simply hover the mouse over the link. This will open a small display showing you the true destination of the link.
Please note: The opinions expressed in Industry Insights published by dotmagazine are the author’s own and do not reflect the view of the publisher, eco – Association of the Internet Industry.




