Trustworthiness Creates Trust
Prof. Norbert Pohlmann from the eco Association and Ulla Coester from xethix Empowerment on the approach IT companies need to take to engender trust.

© olm26250| istockphoto.com
Digital assets require a much higher and, above all, quite a specific level of protection. Since it is now no longer easy for users to effectively verify this, they have few alternatives but to trust that manufacturers are doing everything they can to meet the requirements. Looked at from the other perspective: Manufacturers depend on users to trust them and to actually use their IT/security solutions. Part one of a two-part set of articles by Prof. Norbert Pohlmann from the eco Association and Ulla Coester from xethix Empowerment, examining the approach IT companies need to take to achieve a high level of trustworthiness.
In the future, more and more new value will be created that (only) exists in digital form and, as a consequence, requires much greater and more individual protection. Achieving this level of protection is more complex than it ever was in the analog world – because, on closed company premises, it is more likely to be possible to monitor company assets effectively or to store them securely in safes, and thus to protect them in a way that is easily transparent for management.
In contrast, in the digital world, protection is no longer directly under the control of user companies. Not only are they no longer able to physically verify the protection of their digital assets – they must simultaneously trust that IT manufacturers are doing everything they can to ensure the right approach to the development, selection, and implementation of cybersecurity measures such as encryption, multifactor authentication, or isolating applications. With regard to the future viability of provider companies, it is important to recognise that trust has an impact on company processes at multiple levels. This comes down to the growing vulnerability in the digital realm caused by increasingly adept attacks. The demand for a conscientious approach to cybersecurity calls on manufacturers to take all measures to protect their own companies from attacks. However, they must at the same time develop their IT/security solutions using cutting-edge technical tools, in order to be able to provide the best possible IT technology.
This demonstrates the relevance of trust in the use of IT/security solutions on the part of users, and at the same time underscores the need for companies to act in a trustworthy manner so that this trust is justified.
Why is user trust necessary?
As digitalization accelerates and becomes increasingly complex, innovative IT/security solutions are becoming less predictable from the user’s perspective, with users no longer able to make sense of the IT technology. This brings consequences, a fact which is also shown by the results of the Online Trust Compass of the German Association for the Digital Economy (Bundesverband Digitaler Wirtschaft), in which 46 percent of respondents state that “The rapid change in our living conditions due to increasing mechanization and interconnectivity scares me” [1].
For this reason, it is necessary to design digitalization in such a way that it can be accepted by users. This is an extremely important aspect given that, from their point of view – and simply because they no longer fully understand the IT technology – the use of any IT/security solution is in theory an act of risk. In principle, this is because any decision made without full knowledge of the outcome of the action represents a risk. Although this applies to almost all actions, it is usually not consciously perceived as such. Despite there very often being no certainty regarding the success of everyday actions in terms of the action goal, hardly anyone consistently describes them as risky. Something is only perceived as a risk when there is the danger of loss in the event of an action’s failure – to put it simply, when the individual perceptibly ‘puts something on the line’.
This sensation is subjective and takes on a different hue for each individual. It is therefore important for companies to proceed in a very precise manner in order to build up a basic level of trust in their technology.
Why?
Basically, the hypothesis of future trust between two individuals – i.e. interpersonal trust – is based on the possibility of being able to make an immediate assessment of the other person – for example, on the basis of facial expressions. The ability to trust a stranger can generally be traced back to the human capacity for empathy. In a nutshell: Socialization is anatomically anchored in the brain, from where people can absorb interpersonal information quite effortlessly and thus comprehend the motives of others.
In digitalization, people must be supported in transferring their capacity for trust over to institutions and their IT/security solutions.
The implication for institutions is that they need to very carefully elicit what needs to be done to establish this institutional trust relationship.
Cybersecurity as the basis for trustworthiness?
User trust is built to a large extent on the trustworthiness of IT/security solutions and manufacturer/provider companies. Both the implementation of cybersecurity and the way it is presented are important components of its trustworthiness. (See Fig. 1)
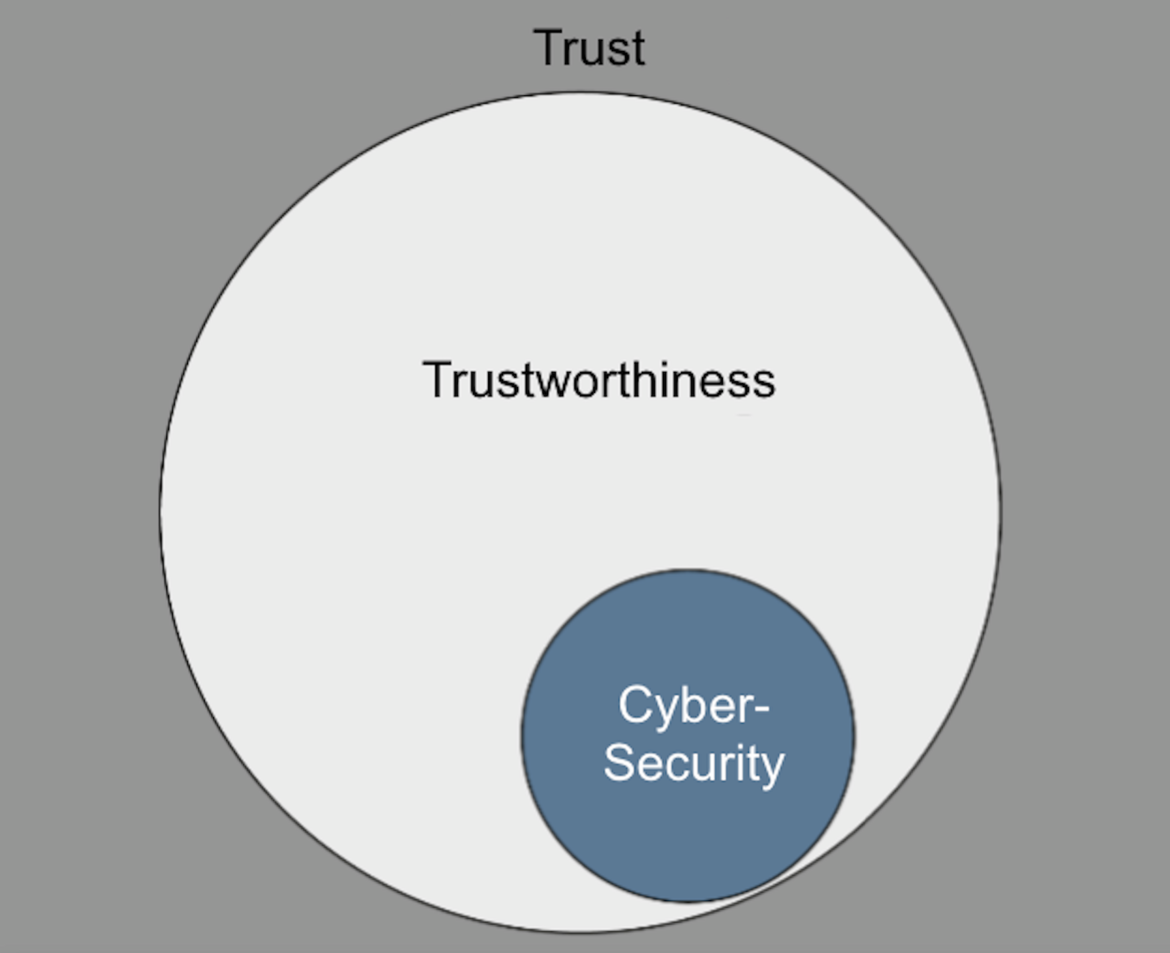
Fig. 1: Relationship between trust, trustworthiness, and cybersecurity
However, in order to credibly demonstrate their trustworthiness in this respect and, in so doing, to manifest trust and acceptance – not only in their company, but also in their cybersecurity solutions or IT/security solutions with cybersecurity mechanisms – additional factors are imperative. These need to offer real verifiability as to whether it is possible to rely on the company and/or on the IT/security solution.
The need for a model of trustworthiness
With digitalization, it is apparent that a strong interdependency has emerged between manufacturers, service providers, and users. The acceptance of IT technology and individual IT/security solutions can also be influenced both positively and negatively within this interrelationship [2].
Here, the following mechanisms take effect: On the one hand, users have significantly more opportunities to exert contol over the actions and performance of manufacturers. This is because users can make their disapproval or negative judgment regarding particular activities of manufacturers known directly via social media. This means that users have a means of direct influence at their disposal.
On the other hand, due to the increased complexity, users have less and less chance of comprehending IT/security solutions. This in part limits their ability to make judgments and in turn reduces their decision-making power. As such, users need to be more ready to trust IT/security solutions in their deployment. This fundamental factor, which is relevant for the success of IT/security solutions and companies, must be considered in a more differentiated way as a result of a further parameter: It must also be taken into account that the interests of the parties involved are sometimes diametrically opposed.
To look at one example: if the manufacturer wants to generate as much customer data as possible with its IT/security solution and use this data for any purpose, this goal is neither in the user’s interest nor in line with the user’s wishes. Whether and to what extent this conflict of interests affects the ability or willingness to trust cannot be answered in a generalized way, as this characteristic varies from person to person. In addition, various other factors play a role. For example, whether the user is, from their point of view, taking a high risk by using the service – but also what the user’s intention is in doing so, and whether the actual fulfillment of the purpose is their top priority.
In any case, it can be assumed that the users themselves generate all the relevant information they need to serve as criteria for decision-making – and thus ultimately for building trust.
Summary: A high level of trustworthiness of an IT/security solution and of the company is necessary to positively influence the acceptance of the IT/security solution. In general, it can be assumed that customer loyalty can be increased through trustworthiness, which at the same time has a positive impact on the acceptance of all products/services of a company.
The foundation: The structure of the model of trustworthiness
The relationships for building trust are shown in the model of trustworthiness (Fig. 2) and are explained below on the basis of the individual factors [3].
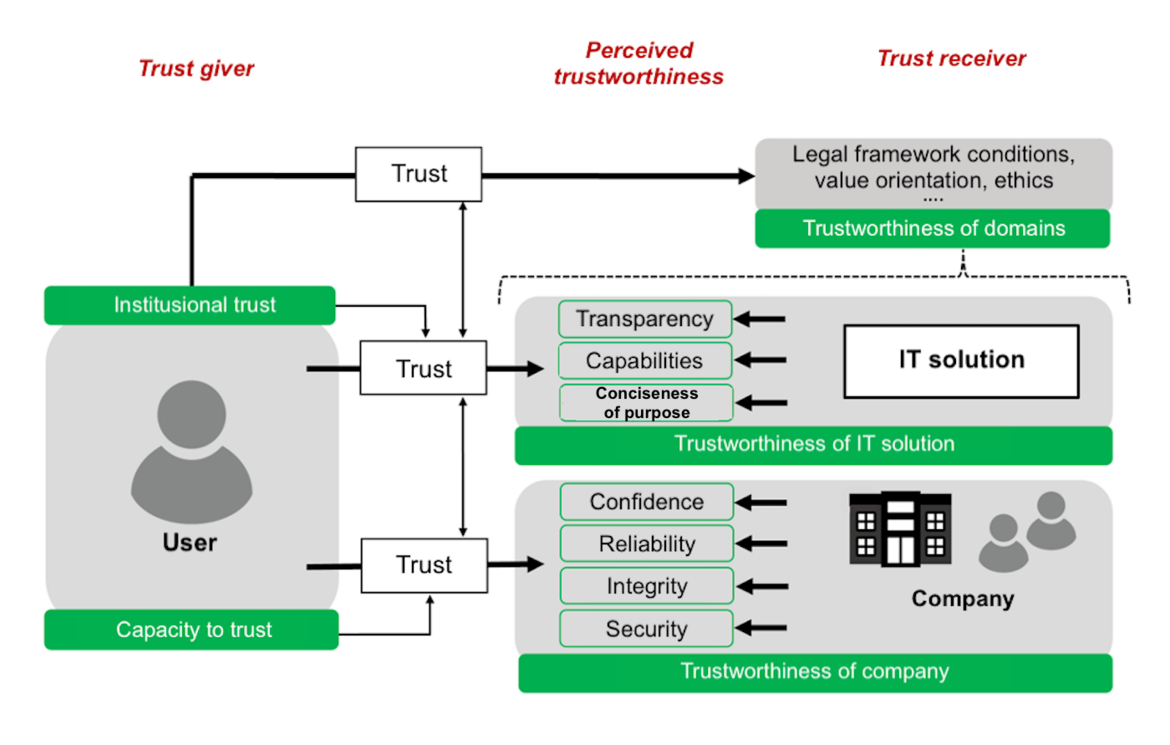
Fig. 1: Model of Trustworthiness
Definitions:
Trust, trust giver and trust receiver: Among other factors, trust refers to the subjective conviction of the correctness of actions. In principle, trust is necessary to reduce complexity and is required whenever the user is confronted with an uncertain situation or when the outcome of an action may be risky. The trust giver’s (user’s) ‘ability to allow’ themselves to trust a trust receiver (company) therefore means the willingness not to question the respective trust receiver and, at the same time, to expose themselves to a certain risk. Particularly in the case of IT/security solutions, an important aspect is that trust can be established with the user primarily on the basis of the trustworthiness of a company and/or its IT/security solutions – i.e., by the fact that companies, as trust receivers, create a basis for trust through a range of measures.
Institutional trust: A basic requirement for people to use IT/security solutions is the promise of added value. Conversely, this means that if users do not gain any value from the use of the solution, they are more critical in their assessment and thus less willing to rely on the respective product per se. In addition, companies need to take further steps to enable users to extend their genuine capabilities to trust in IT/security solutions. This can be enabled by successfully transferring interpersonal trust – i.e. the relationship of trust that develops between people on the basis of certain individual criteria – to IT/security solutions. It is important to note that in the relationship between two people, trust is built based on the ability to empathize and the individually relevant criteria are directly verifiable. This option is not available for IT/security solutions, simply because their behavior or functionality cannot necessarily be verified. Institutional trust is the result of a transfer process – that is, the extent to which users are able and also willing to transfer their trust to institutions such as companies. This trust can be influenced primarily by the company itself, via the IT/security solution (positively), and via the trustworthiness of the domains.
Perceived trustworthiness: Trustworthiness is based on the assumption that it is possible to rely on something specific. As a rule, perceived trustworthiness is based on obvious functionalities of the IT/security solution and measures taken by the company. These are known to the user, as the trust giver, either on the basis of first impressions from their own experience, or via third parties. This clearly shows that it is becoming increasingly important for companies to establish a foundation of trust by explicitly presenting relevant aspects of trustworthiness for both the IT/security solution and the company, so that users can build trust.
Trustworthiness: Essentially, the capacity to trust makes it possible to trust people or companies and to have confidence in them. Based on the individual character of a person or their previous experience, the capacity will be either more dominant or less. In this sense, perceived trustworthiness has an impact on the user’s capacity to trust, and can have a positive impact on it.
Company: A company is considered to be a manufacturer or provider of IT/security technologies, products or services. The above categories are grouped together as IT/security solutions.
Users: Users include all parties who use IT/security technologies, products or services, including user companies.
IT/security solution: In the context of cybersecurity, an IT/security solution is a general application with corresponding cybersecurity mechanisms or a cybersecurity system.
General prerequisites: Domain trustworthiness
It is generally advantageous for companies to act independently in order to generate competitive advantages on the basis of a strong user-centered orientation. However, it is often not easy – or even not possible – to take a pioneering role and thereby shape the market. In many cases, the trustworthiness of an individual company cannot be used to create a general level of trust in, for example, an innovative approach to fundamental IT/security solutions.
Therefore, it is necessary for companies to contribute to the trustworthiness of domains. In other words, it can sometimes be advantageous to create value or implement value concepts collaboratively with other manufacturers, in order to develop the entire industry or domain and thus ensure the successful introduction of new business models or technologies.
In principle, there are several options for establishing trustworthiness for (new) technologies and IT/security solutions. Below are some examples related to domains:
The creation of framework conditions: The state creates the boundary conditions by specifying within the context of a given domain how companies must design the use of technology and IT/security solutions. One example of this is the German IT Security Act, which defines the framework conditions for the security of critical infrastructures. Another example is the European General Data Protection Regulation
Motivating ecosystems: One example in this area is Self-Sovereign Identities (SSI). SSI is intended to establish the basis of a European ecosystem for issuing and verifying digital identities and credentials. Relevant objectives can be achieved through this: among others, the protection of privacy. Because, in this way, users will be able to decide for themselves which application they want to make their digital identity data and other credentials available to, and when. Ultimately, the sovereign handling of a user’s own data also leads to the minimization of dependence on individual providers with a market monopoly, thus promoting the goal of more rapid and independent digitalization. A further advantage: Outdated business models, such as ‘involuntary payment with one’s own data,’ could thus be replaced across the board.
The Gaia-X industry consortium represents another example. Because establishing trustworthiness is not only relevant for new IT technologies: even for already implemented technologies, it is sometimes necessary to redefine standards in a value-oriented manner and in this way to create new standards. In line with the intention of Gaia-X, users should be guaranteed that the IT/security solutions being used comply with European law and ensure data portability, the highest IT security criteria, and clear transparency around data usage. On the basis of this, it is then possible to push for increased storage of data in Europe.
However, it is not always in the interest of the state or consortia to recognize trustworthiness as the most important criterion. Thus, in some cases, measures are taken that are rather counterproductive in this respect and that lead to a weakening of the domain.
Protective mechanisms of the state: A negative example is the use of State Trojans. The use of these weakens the cybersecurity of citizens and companies because knowledge of certain security vulnerabilities is not passed on to the manufacturers, but is employed for State Trojans [4].
Conclusion:
It is necessary to design digitalization in such a way that it can be accepted by users. This requires the development of trust. User trust is built to a large extent on the trustworthiness of IT/security solutions and manufacturer/provider companies. Both the implementation of cybersecurity and the way it is presented are important components of its trustworthiness. The model of trustworthiness provides a framework for developing strategies to engender trust in their company and their solutions. Certain criteria can be used to further define the trustworthiness of companies and their technology, and also what trust actually means.
These criteria will be covered in more detail in the second article of this set.
_____________
References
[1] Online-Vertrauens-Kompass 2020 https://www.bvdw.org/themen/publikationen/detail/artikel/online-vertrauens-kompass/
[2] U. Coester, N. Pohlmann: “Artikelserie über Facetten der Künstlichen Intelligenz”
Warum Vertrauenswürdigkeit und KI unbedingt zusammengehören (Teil 1)
https://www.onpulson.de/63805/warum-vertrauenswuerdigkeit-und-ki-unbedingt-zusammengehoeren/
IT-Systeme: Warum Vertrauen für Unternehmen so wichtig ist (Teil 2)
https://www.onpulson.de/64428/it-systeme-warum-vertrauen-fuer-unternehmen-so-wichtig-ist/
[3] Nils Backhaus: “Nutzervertrauen und -erleben im Kontext technischer Systeme: Empirische Untersuchungen am Beispiel von Webseiten und Cloudspeicherdiensten”, Dissertation, Technischen Universität Berlin, 2016
[4] Tagesspiegel-Background: “Über Zielkonflikte in der Cybersicherheitspolitik wieder mehr diskutieren”,
https://background.tagesspiegel.de/digitalisierung/cybersicherheitspolitik-lauter-zielkonflikte
As founder/CEO of the company xethix Empowerment, Ulla Coester advises on Corporate Digital Responsibility processes, with a focus on trustworthiness/digital ethics. She is also a lecturer in Digital Ethics (Fresenius University of Applied Sciences, Cologne) and a member of the Standardization Evaluation Group 10/IEC: Ethics in Autonomous and Artificial Intelligence Application.
Norbert Pohlmann is a Professor of Computer Science in the field of cybersecurity and is Head of the Institute for Internet Security - if(is) at the Westphalian University of Applied Sciences in Gelsenkirchen, Germany, as well as Chairman of the Board of the German IT Security Association TeleTrusT, and a member of the board at eco – Association of the Internet Industry.