DDoS

Feature "DDoS"
DIA DDoS PROTECT: Closing The Cybersecurity Gap for SMEs
DDoS attacks are rising – and most SMEs lack protection. Serve Bunnik of CITIC Telecom CPC explains how DIA DDoS PROTECT delivers enterprise-grade defense without costly hardware.

Feature "DDoS"
Distributed Attacks = Distributed Liability?
Distributed cyber attacks rely on unsuspecting “contributors”. But are businesses and users aware that they themselves may be legally liable for their “contribution”?

Feature "DDoS"
DDoS: From “Background Noise” to Strategic Threat
Lisa Fröhlich of Link11 warns that AI-powered DDoS attacks now threaten business continuity, reputation, and market position like never before.

Feature "DDoS"
IoT – Pioneering in a Weird Diversified Landscape
The Mirai botnet, making IoT secure, and risks & benefits of e-health: Interview with Peter Meyer, Head of Cyber Security Services at the eco Association

Feature "DDoS"
Mitigating DDos Attacks
Dr. Thomas King, CIO of the DE-CIX Internet Exchange in Frankfurt, speaks to dotmagazine's Judith Ellis about using blackholing to mitigate DDoS attacks at the world’s leading interconnection platform.

Feature "DDoS"
Gridlock: When DDoS Jams Networks
The growing trend of mega Distributed Denial of Service attacks, and the businesses and critical infrastructures vulnerable to it

Feature "Video Streaming"
Quality and Security: Two Steps to Digital Content Delivery Success
Martin Hellmer from Akamai explains the key elements required for delivering high-quality video content to an ever-growing global audience.

Feature "DDoS"
Two Sides of DDoS Attacks: The Largest Attack of All Time and Focus on SMEs
Even though we recently experienced the largest DDoS attack of all time: With Denial-of-Service attacks, it is no longer just a question of bringing down the websites and online shops of large companies. Now, small and medium sized enterprises (SMEs) also need protection, according to Niko Bender from PlusServer.

Feature "Cybersecurity"
Cyber Security & Data Protection in Japan
In Japan as elsewhere, the attack behavior is becoming more sophisticated: Professor Koji Nakao, an eminent Japanese IT security specialist, talks to dotmagazine about differences and similarities in cyber security trends, and about how we need to collaborate to present a counter-measure to cyber threats.

Feature "DDoS"
The Dangers of DDoS Overconfidence
Chris Townsley, EMEA Director at CDNetworks, discusses the rising threat of DDoS attacks, and the misplaced confidence of European businesses in their ability to overcome cyber attacks.

Feature "DDoS"
Carpet Bombing on Digital Infrastructures – Pragmatic Approaches in DDoS Protection and Data Protection
New attack types like Carpet Bombing require specialized protection of hosting & ISP IT landscapes, warns Michael Hempe from Link11 GmbH.

Feature "Security"
The Sectors at Risk from DDoS and Bot Attacks: How to Stop them
Andrew Slastenov from Gcore, on the risks of DDoS and bots and how to protect company systems and networks.

Feature "DDoS"
The Most Dangerous DDoS Attacks of our Time
Dmitry Samoshkin from G-Core Labs advises on what you need to know about DDoS attacks and how to prepare for them.
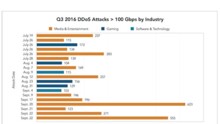
Feature "DDoS"
Optimal Protection against Cyber Attacks
Manfred Fochler from Akamai explores the impact of DDoS attacks, and describes a mitigation case study of the football team FC Bayern Munich

Feature "DNS"
The Domain Name System - Making a Company Website Findable
Sven-Holger Wabnitz explains how DNS works and how important it is for findability and brand identity in the Internet

Feature "Networks"
How can Enterprises Safeguard their Data and Digital Resources?
Dr. Thomas King from DE-CIX explains how an IX platform can shield networks from a range of malicious and accidental security incidents.
Industry Insights "Networks"
Carpet Bombing on Digital Infrastructures – Pragmatic Approaches in DDoS Protection and Data Protection

Feature "E-Health"
Who Wants to Get Hold of Your Health Data?
Maik Morgenstern from AV-Test talks about fitness trackers, smart hospitals, who wants your private health data, and why.

